Table of Content for this Page:
About Fuzzing
“Fuzz testing or Fuzzing is a Black Box application testing technique, which basically consists in finding implementation bugs using malformed/semi-malformed data injection in an automated fashion” OWASP.org.
This is a fun vulnerable box mix of source code inspection, application analysis and fuzzing API endpoint, disclosing sensitive data.
Exploitation
Spawned up the machine, tested the connectivity.

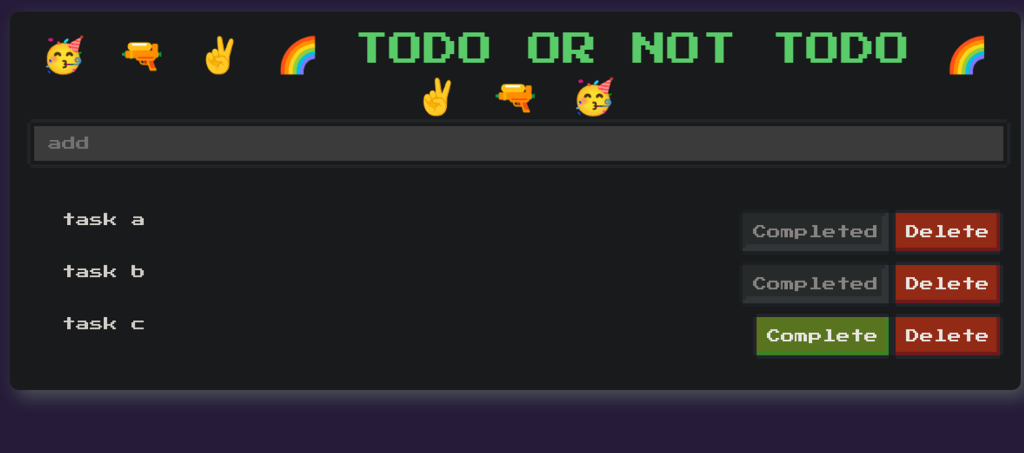
Navigating to the target website, shows as below and an input parameter.

The functionality shows as to-do-list tracker. Inputted some tasks and marked some as completed.
Inspecting the source code, shows as comment JavaScript code that defines a function ‘update’ and then call this function repeatedly every 3 seconds using the ‘setInterval’.
The // comment section suggests that there is a known issue with the getstatus('all') function, and it advises against using it until a specific fix (verify_integrity()) is applied.
The update function seems to be calling another function getTasks with the argument 'user4f375000'. This function likely retrieves tasks associated with the specified user ID.
The update() function is called once initially to fetch the tasks immediately, and then setInterval(update, 3000) is used to call update function every 3000 milliseconds (3 seconds) to fetch the tasks periodically.

The code shows the ‘getTasks ‘ is making API request to /api/list/${endpoint}/ in order to retrieve our to-do-list tasks.
const complete = task => fetch(`/api/complete/${task.id}/?secret=${secret}`, {method: 'GET'})
const delet = task => fetch(`/api/delete/${task.id}/?secret=${secret}`, {method: 'DELETE'})
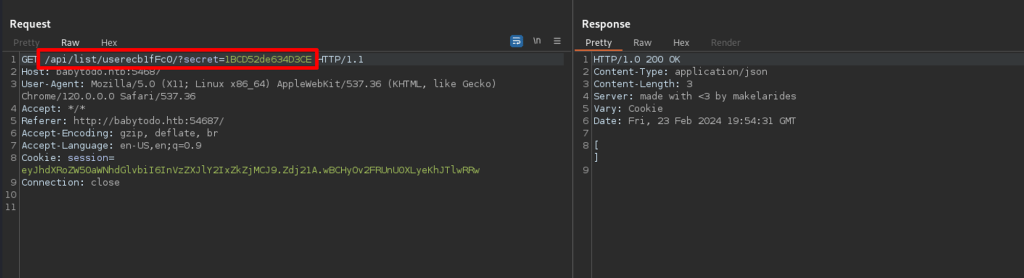
Reviewing the requests intercepted via burp, shows the request being made to specific endpoint with a secret value.
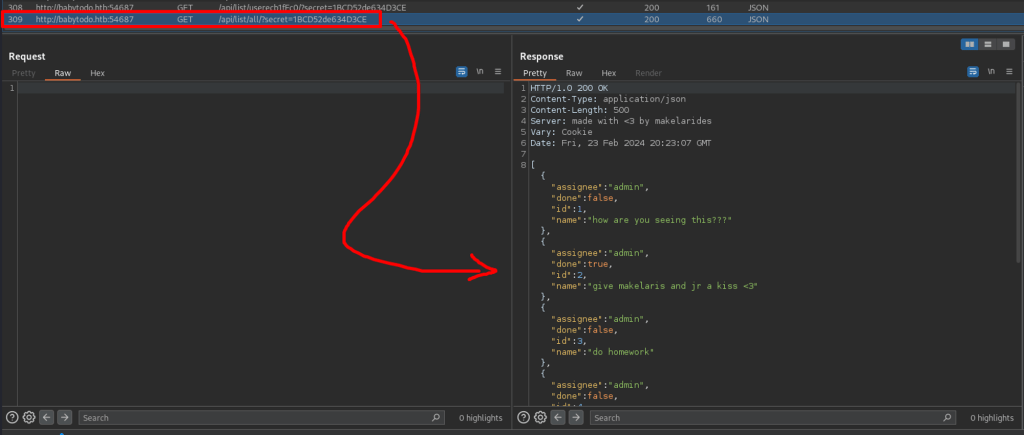
Investigating the endpoint a step further via Wfuzz utility with wordlist objectives.txt, shows the ‘all’ endpoint with 200 response code 500 character.

Visiting the ‘all’ endpoint discloses the tasks and to-do-lists of the users, as we shouldn’t be able to access or read.
Impact
Technical Impacts
- Data Exposure: Fuzzing can reveal directories or endpoints that were not intended to be exposed, potentially leading to sensitive data leakage.
- Security Vulnerabilities: Exposed directories may contain sensitive information or API endpoints that can be exploited by attackers, leading to security breaches.
- Application Stability: Fuzzing can cause unexpected behavior in the application, leading to crashes or instability.
Business Repercussions
- Data Breaches: Exposed directories can lead to data breaches, resulting in loss of customer trust and potential legal consequences.
- Reputation Damage: Data breaches and security vulnerabilities can damage the reputation of the company, leading to loss of customers and revenue.
- Regulatory Non-Compliance: Failure to protect sensitive data can lead to regulatory fines and penalties, such as GDPR or CCPA violations.
- Financial Loss: Data breaches and security incidents can result in financial loss due to remediation costs, legal fees, and loss of business.
Mitigation
- Fix the Vulnerability: Address the underlying issue with
getstatus('all')andverify_integrity()to ensure that the code is secure and works as intended. - Sanitize Inputs: Always sanitize inputs to prevent injection attacks. Ensure that user-supplied data is validated and sanitized before being used in queries or commands.
- Implement Proper Authentication: Use proper authentication mechanisms to verify the identity of users and ensure that they have the necessary permissions to access the data.
- Error Handling: Implement proper error handling to prevent sensitive information from being leaked and to provide meaningful error messages to users.
I hope you find this write up helpful.

