Table of content:
About the vulnerability
XSS (Cross-Site Scripting) is a serious web vulnerability where attackers inject malicious scripts into web pages, potentially stealing sensitive information or taking control of user accounts.
Enumeration
Performing basic enumeration on target (crossfit.htb). There are 3 common ports open. FTP and http protocols worth investigation.
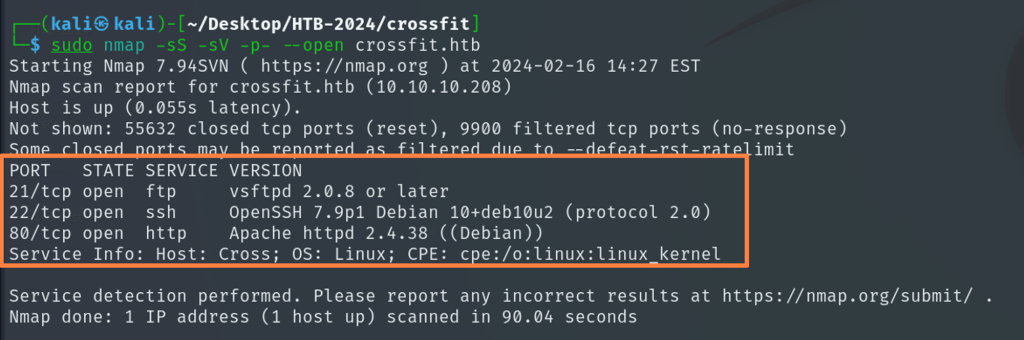
Learning more about the ftp protocol using nmap tool, the scan result shows ssl-certificate and where an email address is leaked with a subdomain as gym-club.crossfit.htb
Visiting the port 80, crossfit.htb domain, it displays default page. I preformed fuzzing for files and directories, but none was discovered useful.
Visiting the subdomain gym-club.crossfit.htb, first by adding it to /etc/hosts file, then browsing to the subdomain, it shows a functional website, worth further inspection.
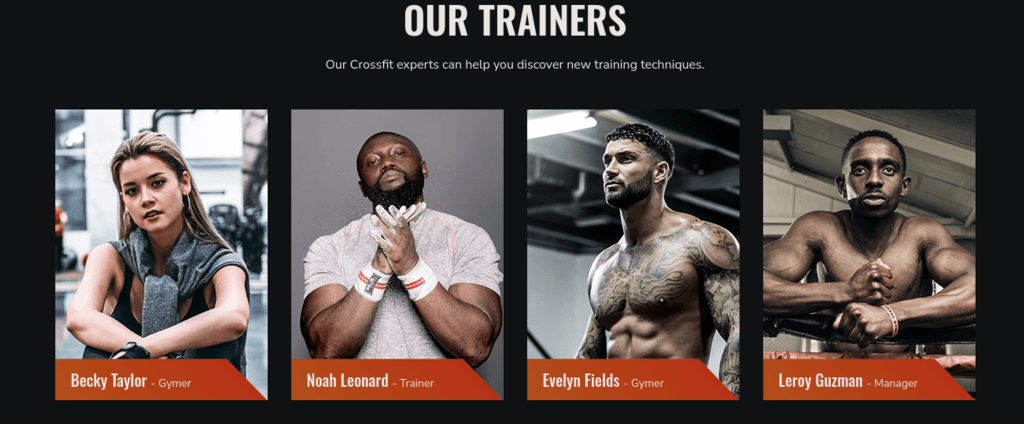
I found some of the trainers name, as possible users… I put them in the try list.
Discovering the vulnerability
Moving on, there is a blog on the following link, where I found an author. http://gym-club.crossfit.htb/single-blogpost.html

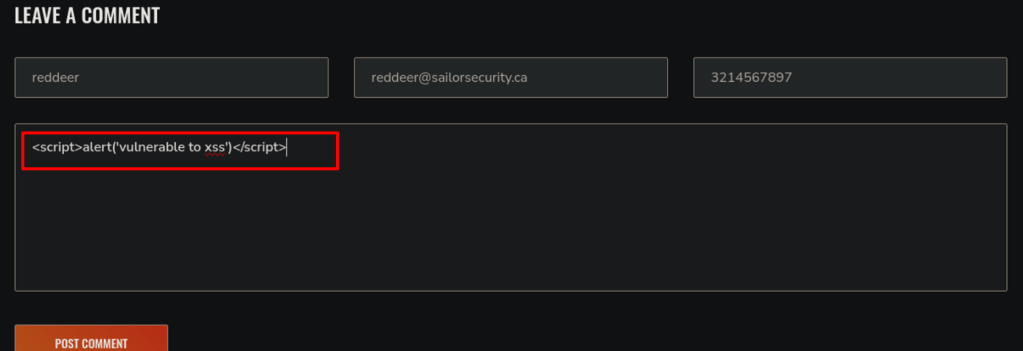
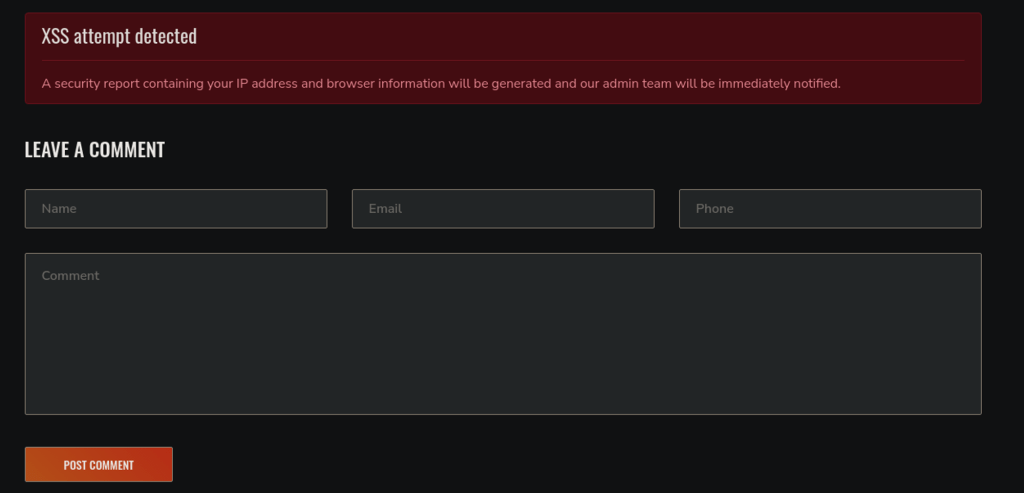
At the end of the blog post, there is a comment section, where I injected xss payload and voilà.
The payload is a simple javascript injection that pops the string called ‘vulnerable to xss’, however, the attempt resulted in the printed message confirming the vulneraability.
Impact
Technical Impacts
- Data Theft: Attackers can steal sensitive data such as cookies, session tokens, or other credentials, leading to unauthorized access.
- User Impersonation: Attackers can impersonate users, perform actions on their behalf, or manipulate their interactions with the web application.
- Website Defacement: Attackers can inject malicious scripts to modify the appearance or content of a website, potentially damaging the organization’s reputation.
- Malware Distribution: Attackers can use XSS to distribute malware, infecting users’ systems and potentially spreading the infection further.
- Session Hijacking: Attackers can hijack user sessions, gaining unauthorized access to sensitive information or performing malicious actions.
Business Repercussions
- Loss of Customer Trust: XSS attacks can undermine customer trust, especially if sensitive information is compromised or if the website is defaced.
- Legal Consequences: Data breaches resulting from XSS attacks can lead to legal consequences, such as fines for non-compliance with data protection regulations (e.g., GDPR, CCPA).
- Financial Losses: Data breaches, website downtime, and reputation damage can lead to financial losses for the organization.
- Reputation Damage: Publicized XSS attacks can damage the organization’s reputation, leading to loss of customers and business opportunities.
- Operational Disruption: Dealing with the aftermath of an XSS attack can disrupt normal business operations, requiring resources and time to mitigate the damage and implement preventive measures.
Mitigation
- Input Validation:
- Validate and sanitize all user input to ensure it does not contain malicious scripts.
- Use strict whitelists for input validation rather than blacklists to prevent bypassing.
- Output Encoding:
- Encode user input before displaying it in the web application to prevent script execution.
- Use appropriate encoding methods such as HTML entity encoding or JavaScript escaping based on context.
- Content Security Policy (CSP):
- Implement a strict CSP to restrict the sources from which scripts can be executed.
- Use CSP directives to limit the types of content that can be loaded and executed on your web pages.
- Secure Cookies:
- Set the
HttpOnlyflag on cookies to prevent them from being accessed by client-side scripts. - Use the
Secureflag to ensure that cookies are only sent over HTTPS connections.
- Set the
- Session Management:
- Use secure session management practices, such as generating unique session IDs and expiring sessions after a period of inactivity.
- Web Application Firewall (WAF):
- Use a WAF to detect and block malicious requests, including those attempting XSS attacks.

